Digital forensics is a vital field that focuses on identifying, recovering, and studying data from digital devices like computers, smartphones, or servers. It plays a key role in solving cybercrimes or understanding security incidents. In this work, many technical terms are used, and one of them is PDU, which stands for Protocol Data Unit.
What is a PDU?
A Protocol Data Unit (PDU) is simply a chunk of data that’s sent over a network. Every time two devices talk to each other say a computer sending a message to a phone that data is wrapped in layers, and each layer follows certain rules or protocols. Each layer builds its own unit of data, which we call a PDU.
Imagine sending a letter: the letter is the data, and the envelope is the PDU. Just like the postal service needs certain information on the envelope to deliver it, a network needs certain information in the PDU to send data correctly. 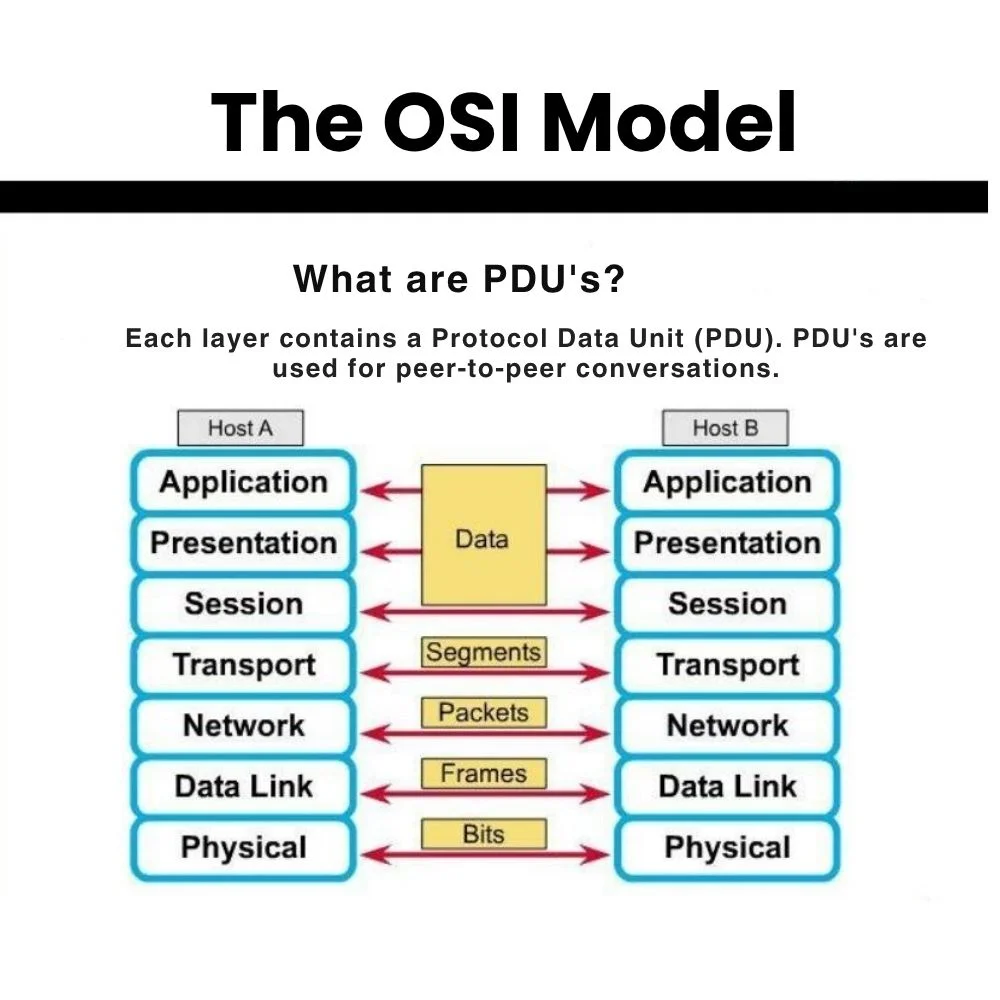
In networking, we often use the OSI model, which has seven layers. Each layer handles a specific part of communication and uses a different kind of PDU:
- Application Layer: uses data
- Transport Layer: uses segments (or datagrams in UDP)
- Network Layer: uses packets
- Data Link Layer: uses frames
- Physical Layer: uses bits
So, a PDU can mean different things depending on which layer you’re working with. But overall, it’s the name for the data being processed or sent at each step.
Why Are PDUs Important in Digital Forensics?
In digital forensics, investigators look for clues about what happened on a device or network. Since PDUs are the basic parts of data transmission, analyzing them helps professionals understand what kind of data was shared, who sent or received it, and when it happened. It can also help detect suspicious behavior.
For example, if someone hacked into a system, a forensic expert might examine captured network data. By looking at the PDUs, they can see the steps taken by the attacker, what commands were run, which files were accessed, and where the connection came from.
PDUs can reveal:
- The type of data sent
- Sender and receiver information
- Time and date of communication
- The protocols involved (e.g., HTTP, FTP, or SMTP)
- Signs of unauthorized or abnormal activity
Common Types of PDUs Used in Forensics
Let’s look at some of the main types of PDUs and how they help in forensic investigations:
1. Data PDUs
These carry user data. Forensics experts may use them to view emails, chat content, file transfers, or browsing activity.
2. Control PDUs
These manage how connections work. For example, TCP uses flags like SYN and ACK to open and close connections. Tracking these helps identify when a session started or ended.
3. Management PDUs
Used in network management, these help monitor the network’s health. If someone tries to change device settings or scan a network, management PDUs can log that action.
4. Network Protocol PDUs
These include IP packets. They help investigators trace where data came from and where it was sent, by checking details like source IP, destination IP, and TTL (Time to Live).
5. Link-Layer PDUs (Frames)
These carry MAC addresses and error-checking info. In some cases, a MAC address can help identify which physical device was involved in suspicious activity.
How Forensic Experts Capture and Analyze PDUs?
To work with PDUs, forensic teams use special tools that capture and record network traffic. Some common tools include:
- Wireshark: A free tool that shows live network data and PDUs
- tcpdump: A command-line tool for capturing traffic, often used on servers
- NetworkMiner: A forensic tool that extracts files and user info from captured PDUs
After capturing the data, investigators review each PDU layer by layer to rebuild activities like logins, downloads, or unauthorized access.
By analyzing PDUs, experts can answer questions like:
- Was confidential data accessed or stolen?
- How did the attacker get in?
- Which systems were affected?
Challenges When Working with PDUs
Even though PDUs are helpful, analyzing them can be difficult. Here are some common issues:
- Encryption: If the data inside a PDU is encrypted, you can’t read it without the right key.
- Too Much Data: A busy network sends thousands of PDUs every second. It takes time to go through them all.
- Unnecessary Traffic: Not all data is important. Forensics teams must filter out regular traffic to focus on suspicious activity.
- Spoofing and Hiding: Hackers can use fake addresses or bounce signals through different systems to hide their identity, making it harder to trace them.
Best Practices for Using PDUs in Forensics
To get the most out of PDU analysis, professionals follow some key practices:
- Use filters in capture tools to narrow down results
- Timestamp everything to match PDUs with events or logs
- Work on copies of data to protect the original evidence
- Take notes on what each PDU shows and what conclusions you reach
- Combine data from logs, access records, and system alerts to build a full picture
Future Outlook
The importance of PDUs in digital forensics will grow as cyber threats evolve. Key future trends include:
- AI Integration: AI and machine learning will help detect unusual PDU patterns faster and more accurately.
- Automation: Tools will automate PDU capture, filtering, and decoding, saving time in investigations.
- Encryption Handling: New techniques will be needed to analyze encrypted PDU data securely and legally.
- Cloud & IoT Forensics: With more devices online, PDU analysis will expand to support varied protocols and traffic sources.
- Legal Compliance: Built-in compliance features in tools will help meet global privacy and legal standards.
- Global Collaboration: Standardizing PDU formats will ease cross-border investigations.
PDUs will remain a core element in uncovering digital evidence and securing network communications.
Conclusion
Protocol Data Units (PDUs) are building blocks of network communication and a powerful source of evidence in digital forensic investigations. By examining PDUs, experts can trace how data traveled, detect unauthorized activity, and piece together the timeline of an event. Though working with PDUs can be challenging due to encryption, data volume, or hidden threats, with the right tools and methods, they become a key resource in understanding and solving digital crimes. Whether you’re in cybersecurity, IT, or just curious about how the digital world works, knowing about PDUs helps you see the big picture of how devices talk and how we can keep that communication secure.