Integrity in cyber security means making sure your data and systems are accurate, trustworthy and protected from unauthorized changes. It’s one of the three key pillars of cyber security, along with confidentiality and availability. Even if no one breaks into your system, a small unauthorized change in your data can lead to huge problems. That’s why ensuring data integrity in cybersecurity is just as important as stopping hackers.
Why Integrity in Cyber Security Matters?
Think of your data like the foundation of your house. If it shifts or becomes unstable, everything built on top of it is at risk. Similarly, if your digital information is changed without permission, it can lead to wrong decisions based on bad data, cause financial losses, damage customer trust and violate legal or industry standards. That’s why maintaining the accuracy and trustworthiness of data is critical.
For example, if someone changes numbers in a financial report or alters a patient’s medical history, it can create dangerous and costly outcomes.
Understanding the CIA Triad and Its Link to Integrity in Cyber Security
The CIA Triad stands for:
- Confidentiality: Keeping information secret from unauthorized users
- Integrity: Making sure the data is correct and unchanged
- Availability: means making sure that authorized users can reach the data and systems they need without delay or disruption.
All three are connected. If one fails, the others are affected. Without system integrity, even well-protected or accessible data becomes unreliable and potentially harmful.
Common Threats to Integrity
There are several ways your data can lose its integrity. Some of the most common threats include:
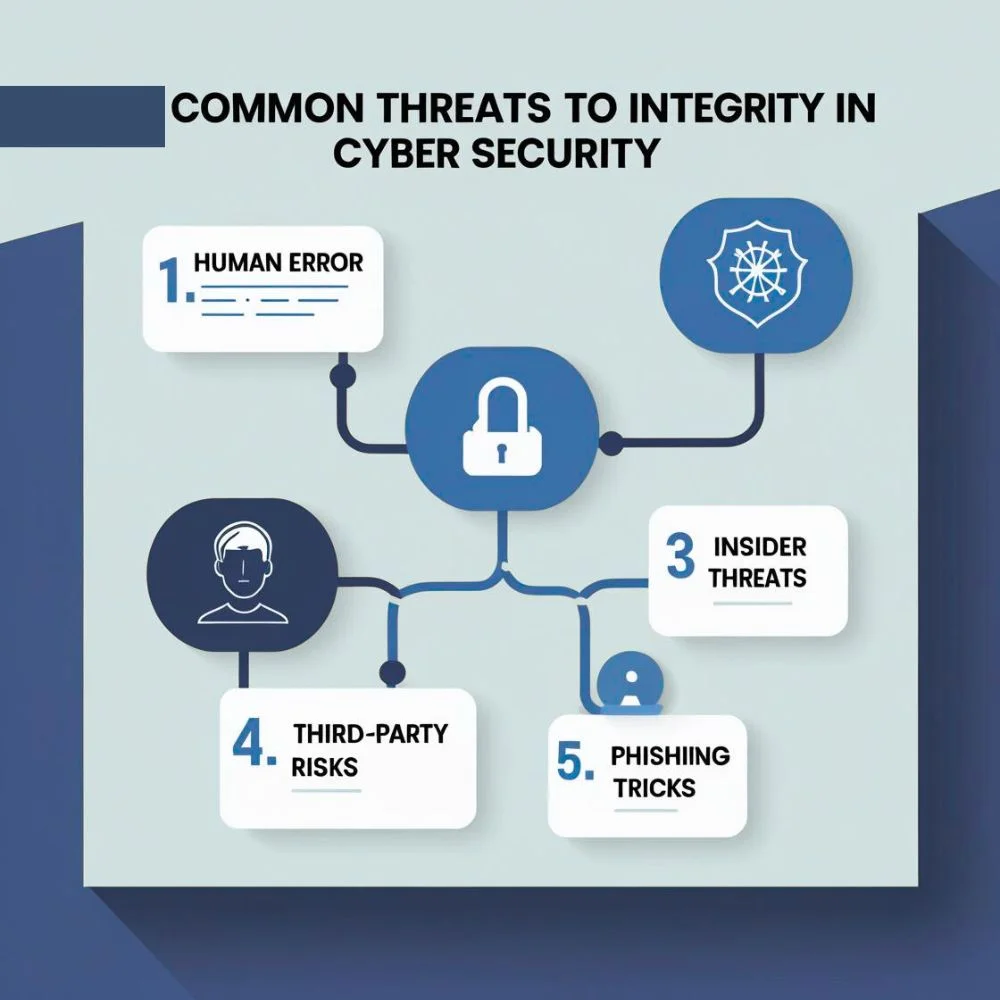
- Human Error: Mistakes like entering the wrong information or deleting the wrong files
- Malware: refers to harmful programs designed to alter, damage or manipulate files and data without permission.
- Insider Threats: Employees or partners who alter data intentionally or carelessly
- Third-Party Risks: Vendors or outside systems with weak security
- Phishing and Social Engineering: Tricks that make someone reveal access details
Each of these can compromise data accuracy if proper controls aren’t in place.
Best Practices to Maintain Integrity in Cyber Security
Now that we understand the threats, here are the best ways to protect and ensure integrity in cyber security.
1. Use File Integrity Monitoring (FIM)
FIM tools check important files and configurations regularly. If anything changes, you get an alert. This helps you catch unauthorized changes early and take action before any harm is done.
2. Apply Cryptographic Hashing
Hashing turns your data into a short code. A minor alteration in the data generates a distinct hash value, making it easy to detect any unauthorized modification. By comparing these codes regularly, you can detect if anything has been altered. This supports information authenticity by detecting tampering fast.
3. Control Who Has Access
Limit access to sensitive data. Only give permission to people who need it. Use strong passwords and multi-factor authentication (MFA) so that even if one security step fails, others protect your data and maintain integrity.
4. Encrypt Data
Encryption converts your information into a secure, unreadable format that only those with the correct access can decode. This protects it from tampering while stored or in transit across networks and reinforces data protection.
5. Regular Backups and Testing
Make frequent backups of your systems and files. Store them securely and test them often to ensure you can restore your data if anything goes wrong. This is a foundational step in protecting cyber security integrity.
6. Keep Detailed Logs
Track who accessed your data, when and what changes were made. Regularly review these logs to spot unusual activity or patterns that might indicate tampering. It helps ensure trusted system operations.
7. Validate and Verify Data
Use input checks to make sure only correct and complete data enters your systems. Regularly verify stored data with trusted sources to catch errors or changes, keeping cyber security integrity intact.
8. Use a Layered Security Approach
Don’t rely on just one tool. Combine different methods like firewalls, anti-malware software, user training and monitoring. This layered method strengthens integrity in cyber security by reducing single points of failure.
9. Build Secure Systems from the Start
When designing software or systems, plan for security early. Include validation checks, audit trails and secure coding practices from the beginning. This early focus embeds integrity in your cyber security framework.
10. Train Your Team
Human error is frequently the most vulnerable aspect of any cyber security system. Teach your employees how to spot phishing, use secure passwords and follow your policies. Awareness reduces mistakes and improves overall protection of cyber security integrity.
Simple Steps to Start Protecting Integrity in Cyber Security
Here’s a quick action plan for businesses or individuals who want to start improving data integrity in cyber security:
- Determine which data is most valuable to your operations and pinpoint its exact storage locations.
- Make sure only trusted people can access it
- Use encryption and hashing tools
- Monitor files for any changes
- Backup your data frequently
- Train your staff on cyber threats
- Check all third-party services for security risks
- Review your policies and update them regularly
Following even a few of these steps can greatly improve integrity in cyber security for your organization.
Example of Compromised Data Integrity
In a recent case, attackers used a phone scam to trick a call center employee at a major airline. They gained access to customer data without hacking any systems. Once inside, they changed booking information and flight details. This shows that even a phone call can harm data integrity if people aren’t trained or systems lack checks.
This example proves why it’s important to train employees regularly, use secure access systems with alerts and monitor for changes in key records. It highlights the importance of maintaining integrity in cyber security in all forms of data handling.
How to Measure Cybersecurity Integrity?
You can’t manage what you don’t measure. So how do you know if your efforts to protect integrity in cyber security are working?
Track these indicators:
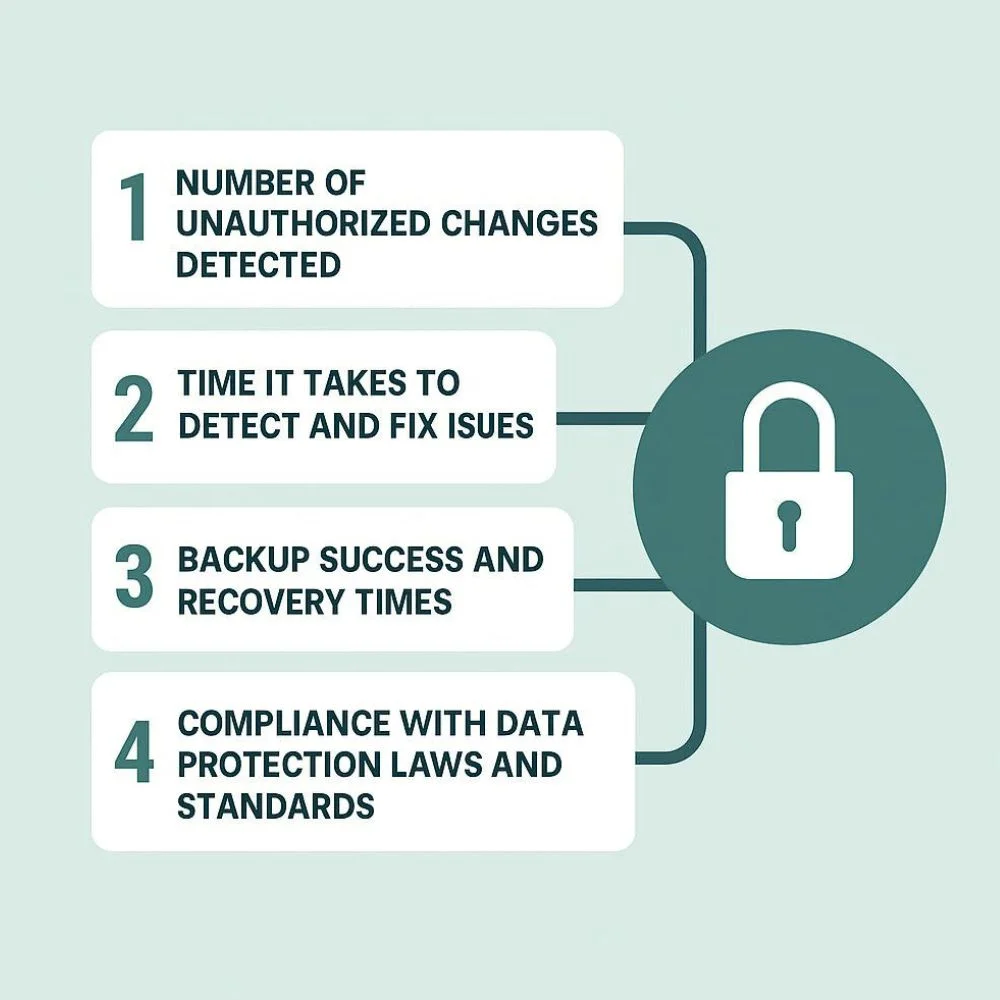
- Number of unauthorized changes detected
- Time it takes to detect and fix issues
- Backup success and recovery times
- Compliance with data protection laws and standards
- Results of internal audits and staff training sessions
The more you track, the better you understand your system’s health and maintain strong cyber security integrity.
Role of Compliance in Integrity in Cyber Security
Compliance with data protection regulations is essential to ensuring integrity in cyber security. Frameworks like GDPR, HIPAA and ISO/IEC 27001 require organizations to implement strict controls for collecting, storing and processing data securely. These guidelines help minimize errors, prevent unauthorized changes and enforce accountability.
By following these standards, organizations not only avoid legal penalties but also demonstrate their commitment to trustworthy data practices. Aligning your cyber security efforts with compliance frameworks builds customer trust, improves system reliability and strengthens overall data integrity.
Final Thoughts
Maintaining information reliability is about creating systems and habits that keep your information honest and accurate. This process includes consistently tracking activity, limiting access, securing data through encryption and training your team effectively. With consistent effort and the right tools, organizations and individuals can greatly reduce the chances of data being tampered with. In today’s digital world, integrity in cyber security is not optional, it’s essential for trust, reliability and long-term success.