Cybersecurity is more important than ever. Whether you’re learning to defend networks, test vulnerabilities, or build a career in ethical hacking, the right tools matter. Pwnbox, a browser-based environment by Hack The Box, offers a secure and convenient way to practice penetration testing no need for virtual machines or complex system setups.
What Is Pwnbox?
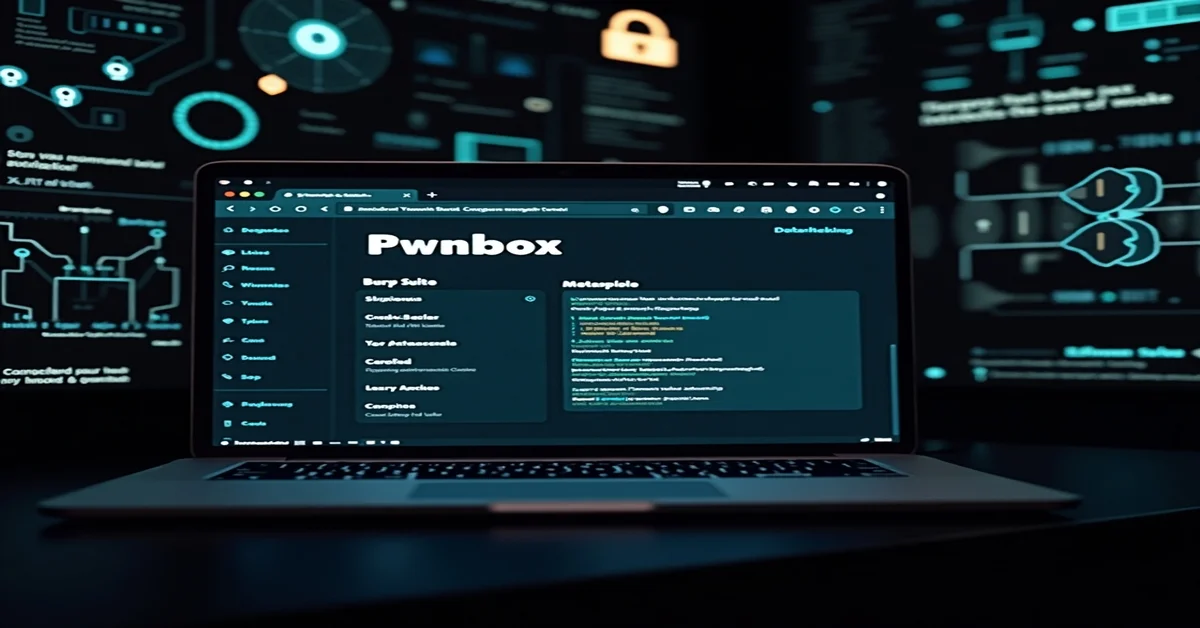
Pwnbox is a cloud-based, pre-configured hacking environment accessible through your browser. It acts like a virtual machine running Kali Linux and provides you with all the tools you need for ethical hacking. You can access it directly from the Hack The Box (HTB) platform, which means there’s no need to install anything on your system. It’s portable, powerful, and perfect for practice.
Why Use Pwnbox?
Using Pwnbox comes with several advantages, especially for beginners or those with limited local resources. Here’s why it’s popular among ethical hackers:
- No setup needed: Everything runs in the cloud
- Always updated: The Latest tools and software are ready to use
- Portable: Use it on any device with a browser
- Safe: Doesn’t affect your main operating system
Integrated with Hack The Box labs and machines
Key Features of Pwnbox
Some of the most helpful features you’ll find in Pwnbox include:
- Full Kali Linux environment
- Built-in tools like Nmap, Burp Suite, Metasploit, Wireshark, and more
- Browser-based remote desktop access
- Easy file transfer with drag-and-drop upload/download
- Secure and sandboxed environment
Use Pwnbox for Cybersecurity Certifications
Pwnbox is highly useful for preparing for certifications like:
- OSCP: Practice buffer overflows, enumeration, and pivoting
- CEH: Practice scanning, enumeration, and exploitation techniques
- CompTIA Pentest+: Run web app scans, brute-force attacks, and network sniffing
- HTB CPTS: Work directly inside HTB’s labs using Pwnbox
No setup distractions, just pure practice.
How to Access Pwnbox?
Accessing Pwnbox is easy if you already have a Hack The Box account. Here’s a simple step-by-step:
- Go to hackthebox.com
- Log in to your account
- Navigate to the “Labs” section
- Select a machine or a module
- Click on the “Pwnbox” tab
- Launch your session and wait for the desktop to load
- You’ll see a Kali Linux interface in your browser
You are now ready to start testing and learning!
Using Pwnbox for Ethical Hacking
Now that you’re inside the Pwnbox environment, here’s how you can begin using it effectively for ethical hacking practice:
1. Reconnaissance
Start by gathering information about your target. Use tools like:
- Nmap for scanning open ports
- Whois, nslookup, and dig for DNS info
- Harvester and Recon-ng for email and subdomain collection
2. Scanning & Enumeration
Once you know your target’s structure, dig deeper:
- Use Nikto to scan for web server vulnerabilities
- Run Dirb or Gobuster to find hidden directories
- Try Netcat for port interactions and banner grabbing
3. Gaining Access
This is where your hacking skills really come into play. Use:
- Metasploit to exploit known vulnerabilities
- Hydra or John the Ripper for brute-force attacks
- SQLMap for database injection testing
4. Privilege Escalation
After you’ve accessed a system, try to gain root or admin privileges:
- Check kernel versions with uname -a
- Use LinPEAS, Linux Exploit Suggester, or WinPEAS
- Review cron jobs, file permissions, and setuid files
5. Maintaining Access & Covering Tracks
This phase is more advanced but crucial in a real-world setting:
- Set up a reverse shell or persistent backdoor
- Clean logs or avoid detection with stealth tools
Remember, these activities should only be done in authorized environments like Hack The Box.
Tips for Using Pwnbox More Effectively
To make the most out of your time on Pwnbox:
- Organize your files into folders by machine name or project
- Take notes using built-in text editors like gedit or install Obsidian
- Regularly update your tools using apt update and apt upgrade
- Use Tmux to manage multiple terminal windows efficiently
- Copy-paste large code or commands via the clipboard tool provided
Comparing Pwnbox with a Local VM
While Pwnbox is great for beginners, here’s how it compares with setting up your virtual machine:
| Feature | Pwnbox | Local VM (e.g., Kali in VirtualBox) |
| Setup Time | None | Requires setup & config |
| Portability | High (browser-based) | Low (device-dependent) |
| Tool Updates | Automatic | Manual |
| Performance | May vary with the internet | Depends on local hardware |
| File Access | Cloud upload/download | Direct file system access |
Use it for quick practice or lightweight tasks. Use a local VM if you need full control and offline access.
Pwnbox Pricing and Access
It is not completely free. While Hack The Box offers limited access to free users, most features and longer sessions are available through HTB’s VIP or VIP+ subscriptions.
Here’s a rough idea:
- Free users: Limited time access or promo periods
- VIP users: Longer sessions with advanced features
- VIP+: Priority access, more machines, and Pro Labs
Is Pwnbox Safe and Legal?
Yes! It is designed specifically for ethical hacking within the Hack The Box ecosystem. It is fully legal and isolated, making it ideal for cybersecurity students and professionals to learn responsibly.
Alternatives to Pwnbox
- TryHackMe AttackBox
- PentesterLab
- Local Kali Linux or Parrot OS setup
- Cyber Range VMs (e.g., BlueTeamLabs)
Limitations of Pwnbox
Like all tools, it has some downsides:
- Dependent on the internet connection
- Can be slower than local VMs
- File transfer limits depend on session size
- Limited customizations compared to local environments
However, for most learners and intermediate users, these are minor issues.
Conclusion
Pwnbox is a powerful tool for ethical hacking, offering a hassle-free, browser-based lab environment. Whether you’re a beginner or an experienced pentester, it simplifies access to hands-on practice without setup issues. To maximize its benefits, practice regularly, approach each machine methodically, and learn from community write-ups and discussions. By consistently experimenting in a safe environment, Pwnbox can become your go-to platform for mastering ethical hacking skills.