Every online action whether sending a message, making a purchase, or accessing a bank account relies on secure systems to protect information. This protection is achieved through cryptographic algorithms, which use mathematical techniques to encrypt and decrypt data. These algorithms ensure that only authorized users can access sensitive information, making it unreadable to hackers or intruders. Though the term may sound complex, the core idea is simple: keep data safe by locking it away from anyone who shouldn’t see it.
What Are Cryptographic Algorithms?
A cryptographic algorithm is a set of mathematical instructions used to transform data so that it becomes hidden or unreadable to outsiders. This process is called encryption. When an authorized user needs to access the original information, a cryptographic algorithm employs a designated decryption key to convert the data back to its readable form, a process known as decryption. Such algorithms serve as the backbone of cybersecurity, contributing to various security mechanisms such as:
- Keep personal information private
- Secure financial transactions
- Prevent unauthorized access
- Protect business and government secrets
- Authenticate users and devices
Why Are They Important?
In the world of cybersecurity, the goal is to make it as difficult as possible for attackers to steal or manipulate data. Cryptographic algorithms do this by creating digital “locks” that are nearly impossible to break without the correct “key.” Even if someone does get access to encrypted data, they won’t be able to make sense of it unless they have the key.
Example
When you send a message on WhatsApp, the app encrypts your message using a cryptographic algorithm. This means only the person you’re messaging can read it. Even WhatsApp can’t see what you wrote. That’s how powerful and important these algorithms are in keeping your conversations private.
Main Types of Cryptographic Algorithms
There are different kinds of cryptographic algorithms, each designed for specific purposes. The most common types are:
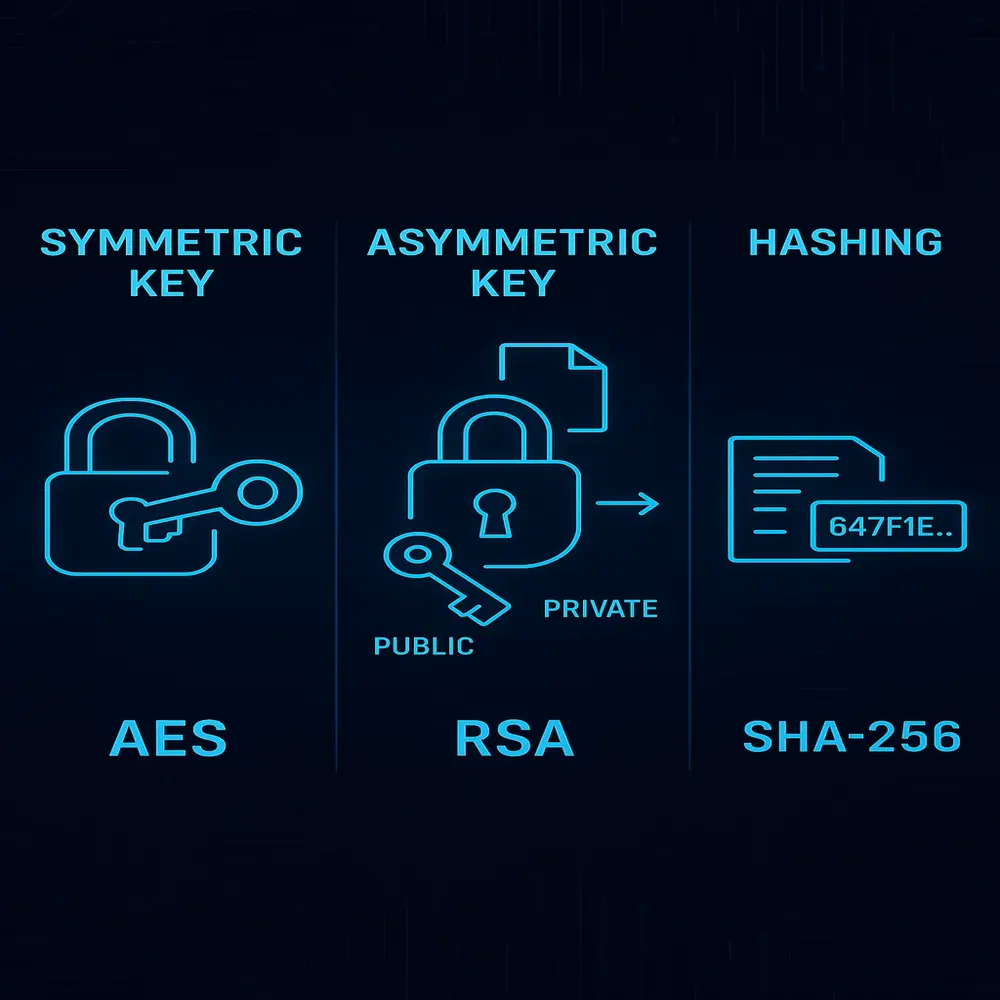
1. Symmetric Key Algorithms
In symmetric encryption, the same key is used to both encrypt and decrypt the data. Think of it like locking and unlocking a door with the same key.
Examples:
- AES (Advanced Encryption Standard)
- DES (Data Encryption Standard)
- Blowfish
Pros:
- Fast and efficient
- Good for encrypting large amounts of data
Cons:
- The key must be shared securely, which can be tricky
2. Asymmetric Key Algorithms
Known as public-key cryptography, this method operates with a pair of keys: a publicly shared key for encryption and a privately held key for decryption. While the public key can be distributed freely, the private key must remain confidential.
Examples:
- RSA (Rivest–Shamir–Adleman)
- ECC (Elliptic Curve Cryptography)
Pros:
- More secure key sharing
- Often used in digital signatures and secure websites
Cons:
- Slower than symmetric encryption
- Not ideal for very large files
3. Hashing Algorithms
Hashing turns data into a fixed-length string of numbers and letters. You can’t turn it back into the original data, but it’s useful for checking whether data has changed.
Examples:
- SHA-256 (used in Bitcoin)
- MD5
- SHA-1
Pros:
- Fast and simple
- Great for verifying file integrity
Cons:
- Some old hashing methods, like MD5, can be broken
Real-Life Uses of Cryptographic Algorithms
Cryptographic algorithms are everywhere, even if we don’t see them. Here are some places where they work silently to protect us:
- Online Shopping: When you enter your credit card details, the website encrypts the data so no hacker can read it.
- Email and Messaging: Secure apps like ProtonMail or Signal use strong encryption to make sure only the intended recipient can read your messages.
- Banking Apps: When you log into your bank account, cryptography helps ensure your username and password are safe.
- Wi-Fi Security: Your Wi-Fi router uses encryption to stop outsiders from stealing your internet or spying on your data.
- Software Updates: Companies use cryptographic signatures to confirm that updates come from a trusted source and haven’t been tampered with.
How does the Process work?
Let’s simplify the process with a basic example:
- Alice wants to send a message to Bob.
- Alice uses a cryptographic algorithm to encrypt the message using Bob’s public key.
- The encrypted message looks like random text to anyone else.
- Upon receiving the encrypted message, Bob applies his private decryption key to unlock its contents.
- As a result, Bob successfully retrieves and reads the original message sent by Alice.
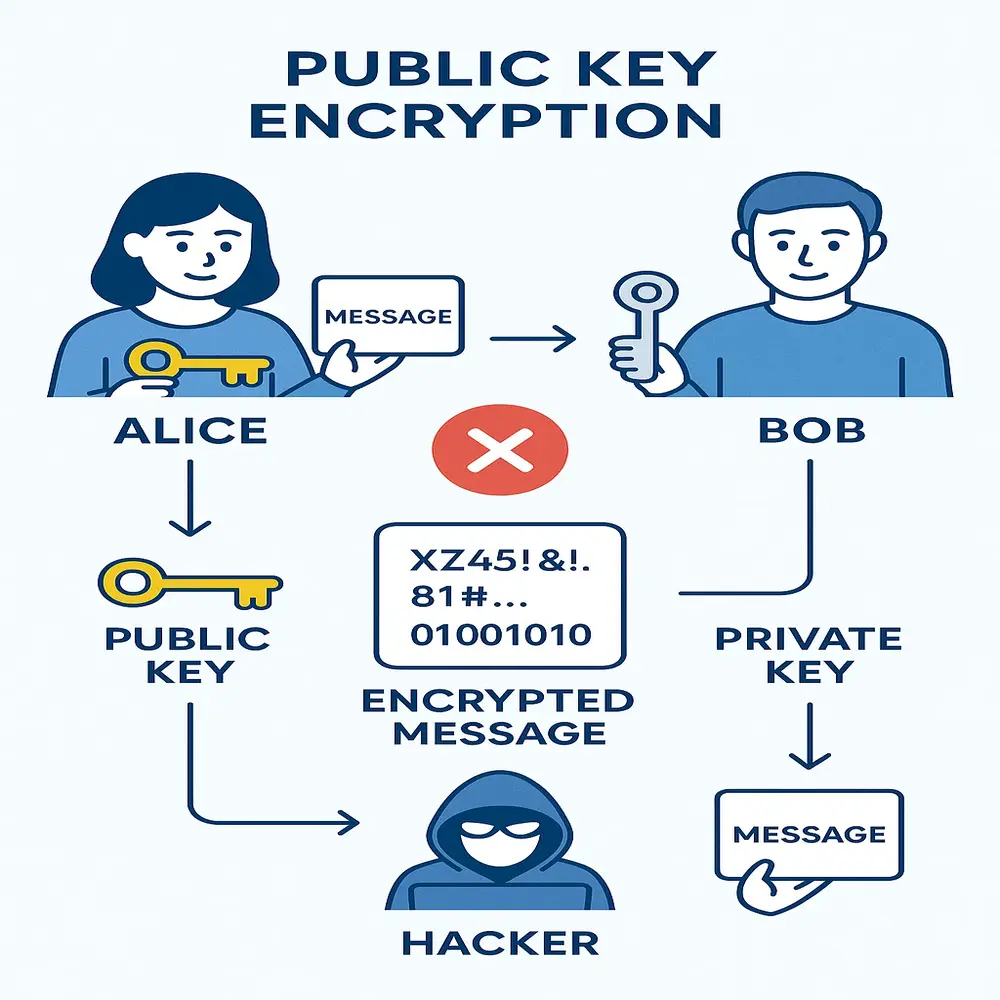
Even if a hacker intercepts the message in the middle, they can’t read it because they don’t have Bob’s private key.
How Are Cryptographic Algorithms Designed?
Creating a cryptographic algorithm takes a deep understanding of math, logic, and computer science. Experts design these algorithms to be:
- Complexity: Algorithms must be mathematically challenging enough to resist unauthorized decryption or brute-force attacks.
- Efficient: They should work fast enough for real-time communication.
- Tested: They are reviewed by cybersecurity professionals around the world.
- Standardized: Organizations like NIST (National Institute of Standards and Technology) approve which algorithms are safe to use.
Challenges in Cryptography
While cryptographic algorithms are powerful, they’re not perfect. Some of the biggest challenges include:
- Key Management: Safely storing and sharing keys is still a major issue
- Performance Consideration: While stronger encryption methods offer enhanced security, they may introduce computational overhead, potentially slowing down resource-constrained systems.
- Quantum Threats: Quantum computers could one day break current encryption
- Human Errors: Misuse or poor setup can weaken even the strongest algorithm
Future Outlook
As digital technology evolves, cyberattack techniques continue to grow in complexity and sophistication. That’s why experts are working on new types of encryption that can withstand quantum computers. To prepare for future threats posed by quantum computing, researchers are developing post-quantum cryptographic algorithms designed to safeguard encrypted data against even the most powerful next-generation computers.
Conclusion
Cryptographic algorithms are like invisible shields that protect us online every day. Whether you’re checking your email, transferring money, or just browsing the web, these smart mathematical tools keep your data safe from prying eyes. You don’t need to be a computer expert to appreciate their value. Just knowing they exist and that they’re working 24/7 to protect you is enough to understand their importance. As the internet continues to grow, cryptography will remain one of the most critical technologies in keeping our digital lives secure.



