If you’ve ever worked with networks, servers, or Windows file sharing, you might have come across Port 445. It may look like just another number, but it plays a big role in how computers talk to each other, especially in the world of Microsoft Windows. To understand this port better, we’ll break it down in simple terms and explain why it matters, how it works, where it’s used, and what security risks are involved.
What is a Port?
In networking, a port acts like a digital gateway for data to enter or leave a device. Each port is numbered from 0 to 65535, with different applications using specific ports. For example, web browsers use ports 80 (HTTP) and 443 (HTTPS), while email relies on ports like 25, 587, and 993. These port numbers guide data to the right service.
Introduction to Port 445
It uses TCP and is mainly associated with the SMB (Server Message Block) protocol, which handles file and printer sharing across Windows networks. In earlier Windows versions, SMB relied on ports 137–139 via NetBIOS, but starting with Windows 2000, Microsoft shifted to it for direct SMB communication over TCP, removing the need for NetBIOS.
What is SMB?
To understand Port 445 better, you need to know a little about SMB. The Server Message Block (SMB) protocol allows devices in a local network to share files, transfer information, and interact with services hosted on other machines seamlessly.
It supports:
- File sharing
- Printer sharing
- Accessing remote services
- Network browsing
So whenever you open a shared file from another computer in your network, SMB is likely doing the work behind the scenes. And it does this through Port 445.
Why is Port 445 Important?
Port 445 is important because it supports many essential functions in a Windows-based network environment. Here’s why it matters:
- Central for File Sharing: It allows easy access to shared files and folders without needing to copy data to each system.
- Printer Sharing: Users can share printers across the network without physically connecting them to each device.
- Domain Logins: In business environments, it plays a key role in domain logins, allowing users to log in to company accounts on any networked computer.
- Remote Admin Tasks: System administrators use it for managing and updating machines remotely.
- Backups and Syncing: Many backup systems use this port to copy files over the network.
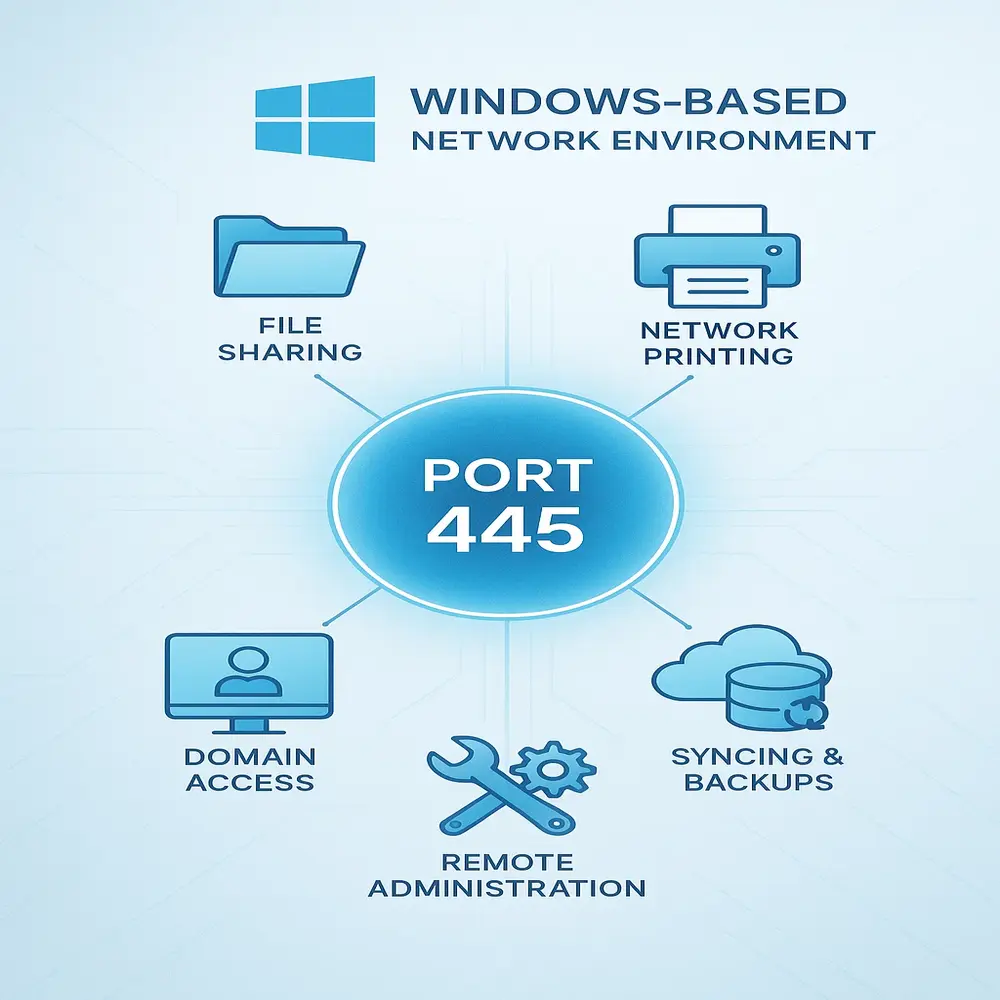
In summary, it is at the heart of many activities that make networking seamless and productive in Windows environments.
Security Risks Related to Port 445
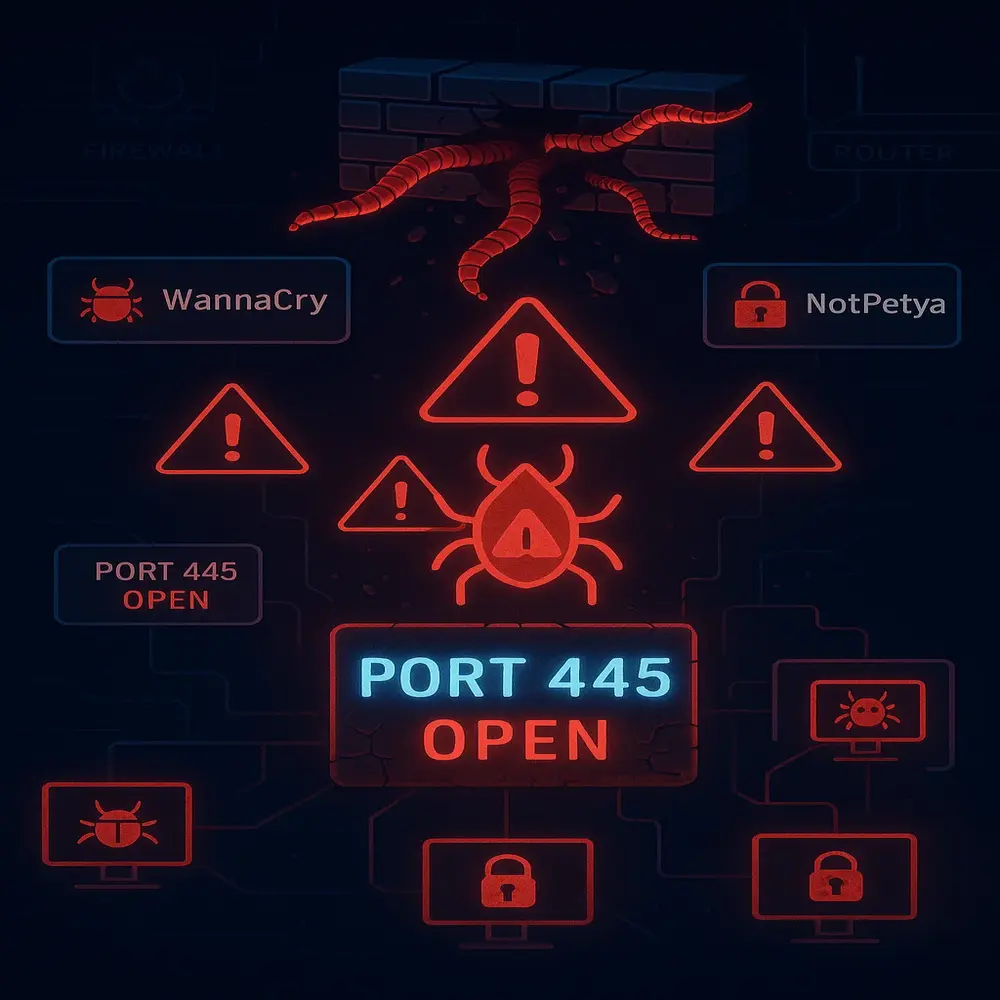
While Port 445 is very useful, it also comes with serious security risks. Because it opens direct communication between computers, it can be an entry point for hackers if not protected properly. Many famous cyberattacks have targeted Port 445.
Major Threats Include
- WannaCry Ransomware (2017): This ransomware exploited a vulnerability in SMB (called EternalBlue) that used Port 445 to spread rapidly across networks.
- NotPetya (2017): Another destructive cyberattack that also exploited the same weakness.
- Worms and Malware: Worms often scan for open Port 445 on the internet and infect any device that isn’t properly protected.
Common Security Problems
- Port 445 is often left open on firewalls and routers, especially in older or unmanaged systems.
- Older SMB versions (like SMBv1) have known vulnerabilities.
- When a network isn’t properly segmented, a single infected device can cause threats to rapidly move across the entire system.
How to Check If Port 445 is Open?
To check if it is active on a Windows system, run the command netstat -an | find “:445” in Command Prompt. If the result displays “LISTENING,” it means that the port is currently active and accepting connections. You can also use tools like Nmap or online port scanners to detect open and potentially vulnerable ports on a network.
How to Protect Systems Using Port 445?
If you’re managing a network or even just a home PC, it’s important to secure Port 445 to avoid attacks. Here are some simple but powerful steps:
- Close Port 445 on Public Networks: Disable this port on firewalls and routers when not needed.
- Disable SMBv1: It’s strongly advised to disable SMB version 1, as it is outdated and contains several well-known vulnerabilities that can be exploited by attackers. Use SMBv2 or SMBv3 instead.
- Use a Firewall: Implement a robust firewall solution to actively monitor and block unauthorized or suspicious access attempts to your system.
- Keep Windows Updated: Install all security patches and updates to protect against known vulnerabilities.
- Use Antivirus and Antimalware Tools: Good security software can detect and block threats trying to exploit Port 445.
- Network Segmentation: Break the network into smaller segments so that if one device is compromised, it doesn’t spread easily.
When Should You Disable Port 445?
While it is useful in many environments, you might consider disabling it if:
- You don’t use file or printer sharing.
- Your device is exposed to the internet.
- You’re setting up a secure or minimal server.
- You want to reduce your attack surface.
To disable it, navigate to your Windows Firewall settings, add a new inbound rule, and configure it to block TCP traffic on this specific port.
Alternatives and Best Practices
Sometimes, instead of using SMB and Port 445, you can go for more secure options like:
- SFTP (Secure File Transfer Protocol)
- RDP with multi-layer authentication
- Cloud file-sharing services like OneDrive or Google Drive
If you must use it, follow zero trust principles, use VPNs, and monitor traffic regularly.
Final Thoughts
Port 445 plays a vital role in Windows networks, primarily supporting file and printer sharing between connected systems. Despite its importance, it’s a common target for cyberattacks and must be secured. Understanding its function helps users and admins make safer decisions. With proper updates and precautions, its benefits can be enjoyed with minimal risk.