If you’re working with Microsoft 365 and need to find out who did what, when, and where, whether for security, compliance or troubleshooting, then the Search‑UnifiedAuditLog command in PowerShell is your best friend. It helps you search audit logs across different Microsoft 365 services like Exchange, SharePoint, OneDrive, Teams and Azure Active Directory.
What is Search‑UnifiedAuditLog?
Search‑UnifiedAuditLog is a PowerShell command (called a cmdlet) that lets you search the Unified Audit Log in Microsoft 365. This log keeps track of nearly every user and admin action across the system. Whether someone deleted a file, changed a mailbox setting or logged in from an unusual location, this command can help you track it.
How UnifiedAuditLog Works in Microsoft 365?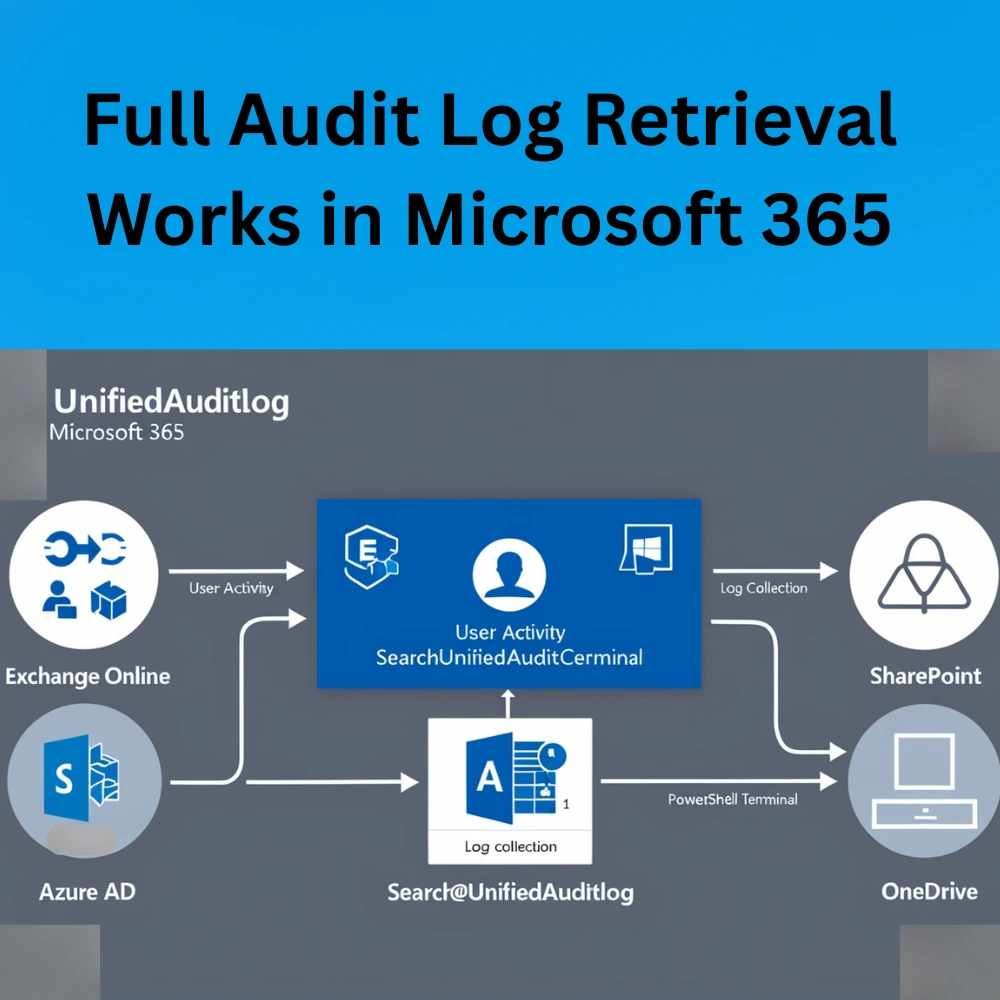
The UnifiedAuditLog collects and stores activity from services like:
- Exchange Online (mailbox operations, email access)
- SharePoint/OneDrive (file edits, deletions)
- Azure AD (login attempts, MFA events)
- Teams (chats, meetings)
- Microsoft Purview & Defender (policy changes, alerts)
Every activity generates a log entry that gets recorded and made available for retrieval using the Search-UnifiedAuditLog command.
Why Use It?
Many people use this command for:
- Security investigations
- Legal or compliance audits
- Monitoring user or admin activity
- Creating automated audit reports
Before You Start
There are a few things you should check before you use Search‑UnifiedAuditLog:
- Audit Logging Must Be Enabled: Most Microsoft 365 setups have this turned on by default, but it’s good to double-check.
- Correct Permissions: Your account must have the Audit Logs or View-Only Audit Logs role in Microsoft 365 or the compliance center.
- PowerShell Access: You need to connect to Exchange Online PowerShell to run the command. Use modern authentication (especially if multi-factor authentication is enabled).
Testing UnifiedAuditLog in Real Scenarios
Before deploying in live environments, admins can simulate test scenarios:
- Create a test user who deletes and uploads files
- Send emails from shared mailboxes
- Apply policy changes as an admin
Then, use Search-UnifiedAuditLog to verify that all actions appear correctly in the logs.
Filtering Data Using UnifiedAuditLog
Refining your search is key when using the UnifiedAuditLog. Useful filters include:
- -Operations “FileDownloaded”, “SendAs”
- -UserIds to trace specific users
- -RecordType to narrow to services like Exchange or SharePoint
- -FreeText to search for file names or keywords
Filtering helps avoid data overload and ensures targeted investigation.
Exporting Results from UnifiedAuditLog
After retrieving the data, most admins export logs to CSV for:
- Manual review in Excel
- Visual dashboards in Power BI
- Long-term storage for compliance purposes
This allows for easy sorting, filtering, and sharing with relevant departments.
Common Issues with UnifiedAuditLog
Some common problems users face include:
- Logs missing for the last few hours (due to delay in data ingestion)
- Hitting the 5000 record limit without pagination
- Not seeing shared mailbox actions (mailbox auditing not enabled)
These can be solved by smaller time slices, using ReturnLargeSet, or checking audit policies.
Automating UnifiedAuditLog
Many organizations automate log retrieval using scheduled PowerShell scripts. These scripts:
- Run daily/weekly to export logs
- Automatically filter by operation or service
- Email or store the CSV results securely
Automation helps maintain continuous visibility into activities across Microsoft 365.
Visualizing UnifiedAuditLog Data After Full Audit Log Retrieval
Once logs are collected, visualization helps convert raw data into insights. You can:
- Use Excel pivot tables to show user actions by type
- Create charts showing peak activity hours
- Visualize policy change frequency
This makes the UnifiedAuditLog not just a tool for forensics but also one for user behavior analytics.
Basic Structure of the Command
Here’s a basic version of the command:
Search-UnifiedAuditLog -StartDate “2025-06-01” -EndDate “2025-06-15” -ResultSize 5000
This command fetches the last 15 days of audit data, returning up to 5,000 results. But this is just the start. You can use many other options to narrow or expand your search
Important Parameters You Can Use:
- Start Date and End Date: Define the time period you want to search.
- User Ids: Filter by specific user email addresses.
- Operations: Look for specific types of activities like “FileDeleted” or “SendOnBehalf”.
- Record Type: Focus on a specific service (like Exchange, SharePoint, etc.).
- Free Text: Search using keywords.
- Result Size: Set how many entries you want to retrieve (up to 5000 per call).
- Session Command Return Large Set: Use this to retrieve more than 5000 results through pagination.
- Session Id: Use a unique ID to track sessions for large data extractions.
Getting the Full Audit Log (Large Result Sets)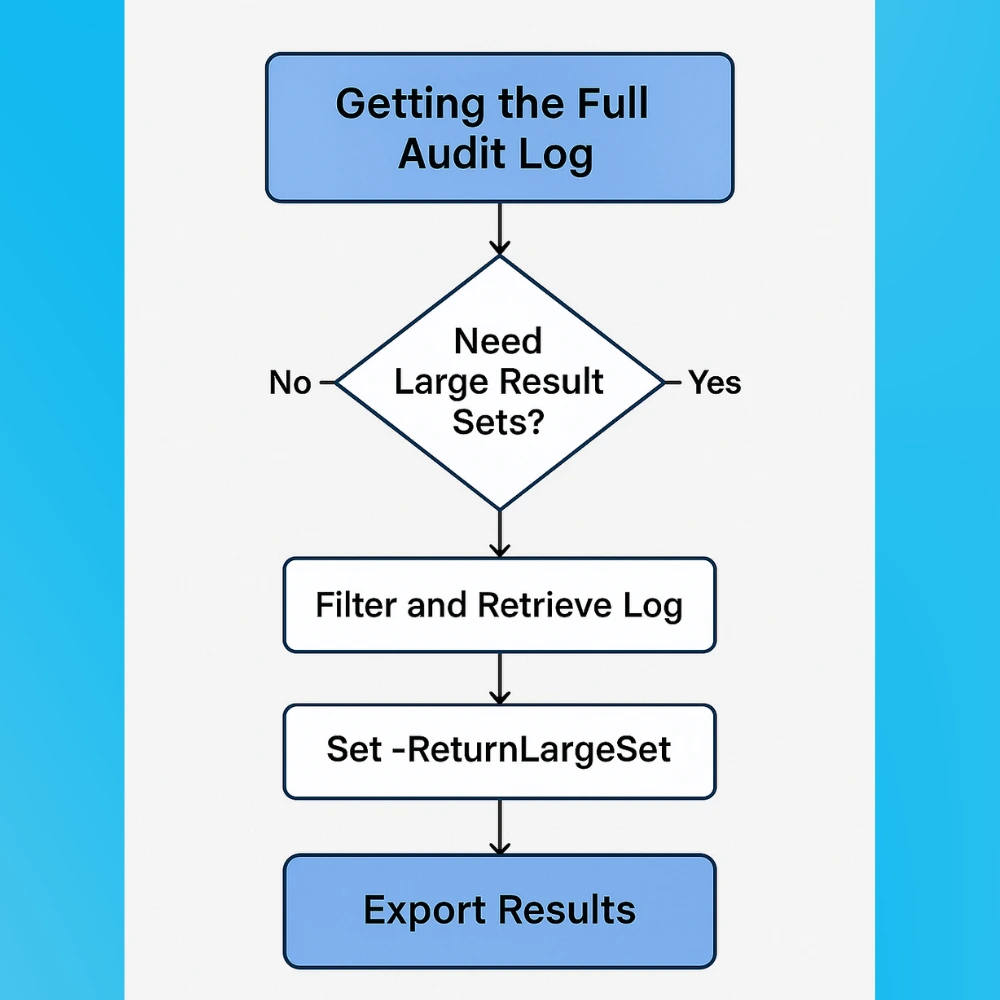
When you’re performing full audit log retrieval in Microsoft 365, one of the biggest challenges is handling large result sets. This is especially true for organizations with hundreds or thousands of users, where a single day’s worth of activity can generate tens of thousands of log entries.
Default Limitations of Search‑UnifiedAuditLog
Here are the key limits you must understand:
- Maximum result size per call: 5000 records
- Total result cap without large set flag: 10,000–50,000 depending on load
- Retention delays: Audit events may appear with latency of up to 24 hours
- Retention period: Default is 90 days, but can be longer with premium licenses
If you try to pull all audit data in one go using broad dates or filters, you will miss data due to these caps.
Tips for Better Results:
- Use Filters: Always try to use UserIds, Operations, or RecordType to narrow your search and reduce system load.
- Shorten Time Windows: If you’re getting 5000 results in one slice, that means more data is being left out. Cut your interval down to 30 or 15 minutes.
- Use Unique Session IDs: This keeps each batch separate and avoids errors.
- Post Sorting: Since the ReturnLargeSet method doesn’t sort data by date, you may want to sort by CreationDate later using Excel or Power Query.
Alternatives to Consider
If you’re doing this regularly or need real-time access, look into:
- Microsoft 365 Management Activity API (for continuous export)
- Microsoft Purview portal for visual log searches
- Third-party SIEM tools like Splunk or Sentinel for automated alerting
Final Words
The Search‑UnifiedAuditLog cmdlet is a powerful tool for anyone responsible for Microsoft 365 security and compliance. Once you understand how to use its parameters and combine it with scripting, you can uncover exactly what’s happening in your organization from unauthorized file deletions to mailbox tampering. By automating and exporting your search data, you’ll be one step closer to a more secure and well monitored system.