In today’s rapidly evolving digital landscape, organizations are seeking ways to deploy and manage devices at scale without increasing operational overhead. One of the key enablers of this transformation is Zero Touch Provisioning (ZTP). This modern method of automating device configuration and deployment allows IT teams to streamline onboarding processes and minimize human intervention.
Why Zero Touch Provisioning Matters?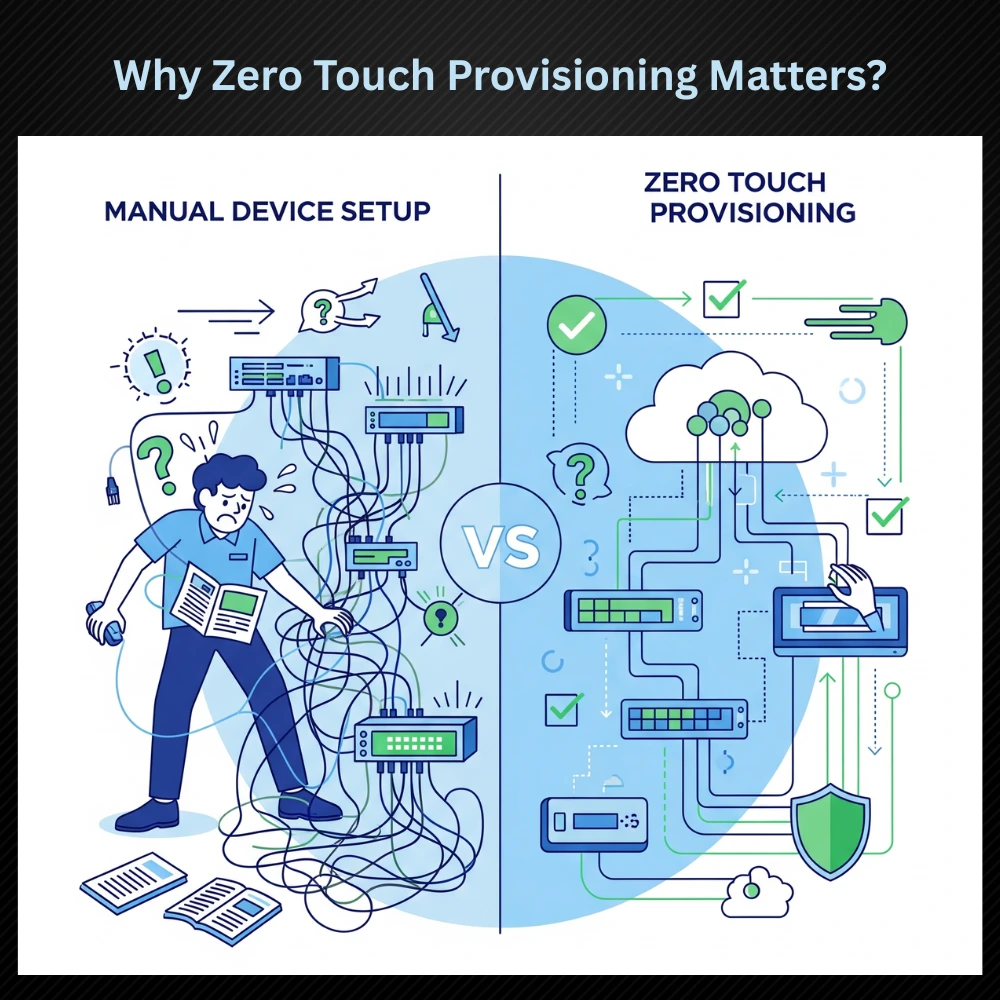
Traditionally, setting up network or IT hardware involved a lot of hands on work. Engineers would need to manually configure settings, load software and ensure compatibility. In large enterprises or distributed environments with hundreds or thousands of devices, this method is both time consuming and error prone.
Zero Touch Provisioning removes these limitations by providing:
- Faster deployments: Devices are up and running in minutes.
- Consistency: Eliminates configuration drift and human error.
- Scalability: Easily handles thousands of endpoints.
- Reduced operational cost: Less on-site IT staff required.
- Enhanced security: Devices are configured using pre-defined secure templates.
How Zero Touch Provisioning Works?
The process of ZTP is based on automation workflows that kick in the moment a new device connects to the network. While implementation can vary by vendor and environment, the general process follows these steps:
- Device Initialization: The device is turned on and connected to the network, where it uses DHCP (Dynamic Host Configuration Protocol) to receive an IP address and discover the provisioning server.
- Server Communication: The device contacts the provisioning server, typically through secure HTTP or FTP protocols. It sends identifying information such as serial number, MAC address, or device type.
- Configuration Retrieval: Based on the device’s identity, the server sends back a specific configuration file, firmware update, or software package.
- Device Configuration: The device downloads the configuration and applies it automatically. This may include interface settings, routing protocols, security policies, and access credentials.
- Validation and Reporting: After setup, the device reports back to the server confirming successful provisioning. Logs are generated for auditing and troubleshooting.
Key Components of ZTP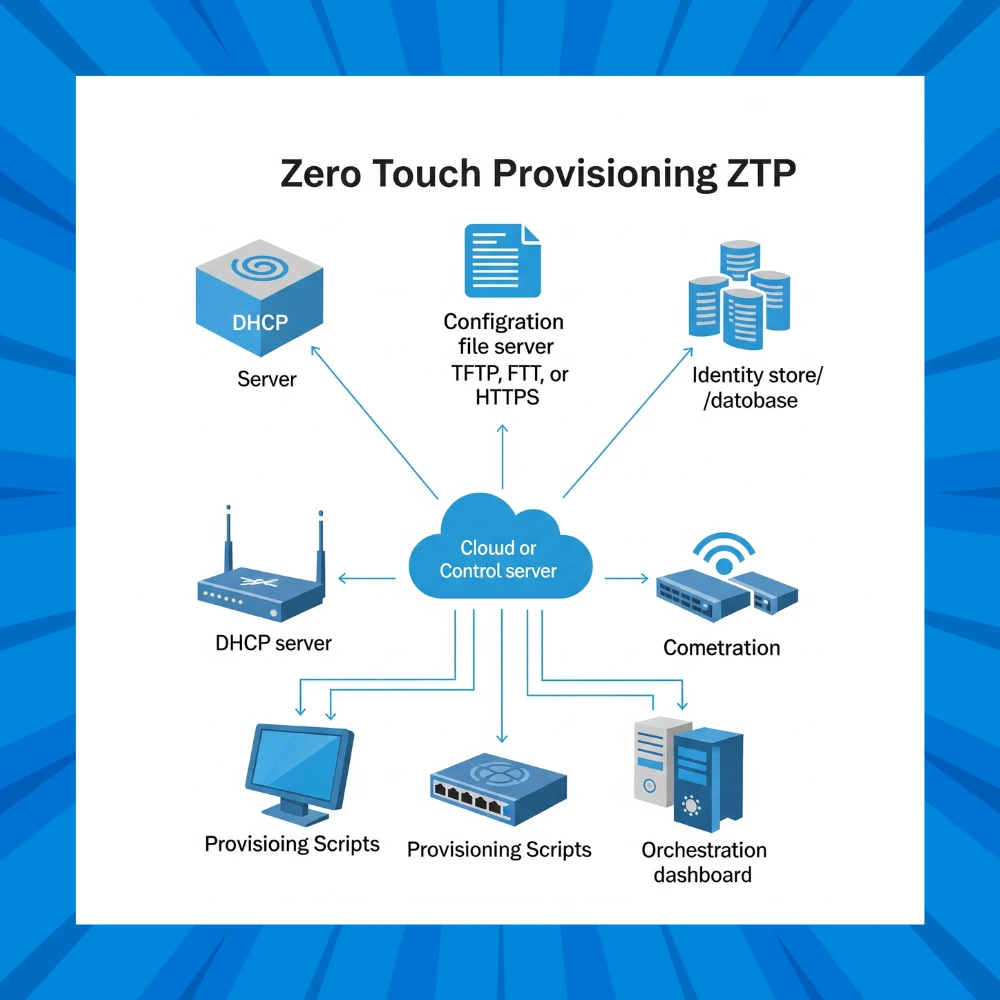
- DHCP Server: Assigns an IP address and delivers information about the configuration server.
- TFTP/FTP/HTTPS Server: Hosts the configuration files and software updates.
- Provisioning Scripts: Define the exact configuration to be applied.
- Device Identity Store: A database mapping device details to their configurations.
- Orchestration System: Manages workflows and ensures process completion.
Benefits of Zero Touch Provisioning
Zero Touch Provisioning provides a wide range of benefits for businesses in various sectors.
1. Time and Cost Efficiency
Manual provisioning can take hours or even days. ZTP allows simultaneous configuration of multiple devices, greatly cutting down the overall deployment time.
2. Reduced Human Error
Because the provisioning process is automated using pre-defined templates, it eliminates configuration mismatches, security loopholes, or missed updates that often occur with manual processes.
3. Centralized Control
ZTP allows IT teams to manage device provisioning from a central location. Whether deploying routers in a remote office or IoT sensors across smart buildings, control remains centralized.
4. Improved Security
Using secure protocols and digital certificates, ZTP ensures that the devices receive authenticated configurations, protecting the network from unauthorized access.
5. Scalability
ZTP supports rapid growth. As more devices are added, the process remains consistent, making it ideal for large enterprises, service providers, and edge computing environments.
Side-by-Side Comparison: ZTP and Legacy Provisioning
To better understand the value of Zero Touch Provisioning, the following table compares it with traditional provisioning methods across critical features like setup time, scalability, security, and error rate.
| Feature | Traditional Provisioning | Zero Touch Provisioning (ZTP) |
| Setup Method | Manual configuration by IT staff | Automated via pre defined scripts and servers |
| Time Required per Device | Hours to days | Minutes |
| Human Intervention | Required on site | None (fully automated) |
| Configuration Consistency | Varies per technician | Uniform and standardized |
| Scalability | Limited labor intensive | Highly scalable, ideal for large deployments |
| Security Risk | Higher manual errors, inconsistent policies | Lower template based, encrypted provisioning |
| Error Rate | High (human error prone) | Low (scripted and repeatable process) |
| Initial Setup Complexity | Low | Medium—requires infrastructure and planning |
| Ideal Use Cases | Small networks, ad hoc deployments | Large-scale enterprise, edge, IoT, multi branch |
| Long-Term Maintenance | Difficult requires frequent manual updates | Easier centralized updates and automation |
Real World Use Case
Zero Touch Provisioning is increasingly used in the following scenarios
- Telecom and Service Providers: To deploy customer premises equipment (CPE) like modems and routers without sending technicians.
- Retail Chains: To configure network gear across hundreds of stores.
- Smart Cities: For onboarding thousands of IoT sensors and edge devices.
- Data Centers: To automate server provisioning during scaling or disaster recovery.
- Corporate Branch Offices: To roll out secure networking gear and VPN connections without IT staff on-site.
Challenges in Implementing ZTP
Despite its advantages, ZTP may face several challenges if not implemented properly:
- Initial Setup Complexity: Establishing servers, templates, and workflows can be complex and require expert planning.
- Vendor Compatibility: Different vendors may have different ZTP standards or capabilities, requiring integration efforts.
- Security Risks: Without proper authentication and encryption, ZTP processes may be vulnerable to spoofing or unauthorized configuration.
- Network Dependency: ZTP requires a stable network and access to provisioning servers; disruptions can affect deployment.
Workflow Of Zero Touch Provisioning (ZTP)
ZTP Is a Key Enabler for Network Automation
Zero Touch Provisioning is not just about convenience, it’s a critical component of network automation strategies, especially in modern SDN (Software Defined Networking) and NFV (Network Functions Virtualization) environments. It complements other automation tools like Ansible, Chef and Puppet by automating the earliest stages of device setup (Day 0 to Day 1 automation).
Security in ZTP
Security is a core consideration in ZTP processes. Without proper safeguards, attackers could intercept or spoof configuration files. Key security measures include:
- Device authentication (via serial number, MAC address, or digital certificates)
- Encrypted configuration file delivery (HTTPS, SFTP)
- Integrity checks (hash based validation or digital signatures)
- Role based access control (RBAC) on provisioning servers
- Cisco, Juniper and Arista all implement Secure ZTP protocols that prevent unauthorized provisioning.
Common ZTP Protocols & Technologies
| Technology | Purpose in ZTP |
| DHCP | Assign IP addresses and provide boot server info |
| TFTP/FTP/HTTPS | Transfer configuration files to device |
| SNMP/NETCONF | Used for remote management or monitoring |
| Python/Bash Scripts | Define the provisioning logic and templates |
| TLS/SSL | Ensure secure file delivery and encryption |
Future Trends in ZTP

- AI Driven ZTP: Using artificial intelligence to dynamically create optimized configurations based on usage patterns.
- Cloud Native ZTP: Hosting provisioning services on public or private clouds for greater flexibility.
- GitOps Integration: Managing configuration files via version controlled repositories like Git, enabling seamless rollbacks and audits.
- Zero Trust Security: Incorporating policy based access control at the provisioning level for enhanced security.
Conclusion
Zero Touch Provisioning is no longer a niche capability, it’s becoming an essential feature in modern IT and networking environments. By automating the deployment and configuration of devices, ZTP helps organizations save time, reduce costs, eliminate human error and improve security. As businesses continue to scale and the demand for fast, secure and consistent provisioning grows, ZTP will play a critical role in building resilient and agile digital infrastructures.
Whether you’re an enterprise expanding globally or a startup deploying IoT devices, Zero Touch Provisioning ensures that your infrastructure is ready to grow without the hands on hassle.



