In today’s digital age, our devices are gateways to our personal and professional lives. However, lurking in the shadows of the internet are malicious programs designed to exploit this access. One such threat is the Remote Access Trojan, commonly known as a RAT. This article aims to demystify RATs, explaining what they are, how they operate, the dangers they pose, and how you can protect yourself all in straightforward terms.
What Is a Remote Access Trojan?
One kind of malicious software that enables thieves to take over your computer or device without your knowledge is called a Remote Access Trojan (RAT). Unlike viruses that replicate themselves, RATs are more like spies, silently infiltrating your system to monitor activities, steal information, or cause harm. They often disguise themselves as legitimate software, making them difficult to detect.
Types of Remote Access Trojans
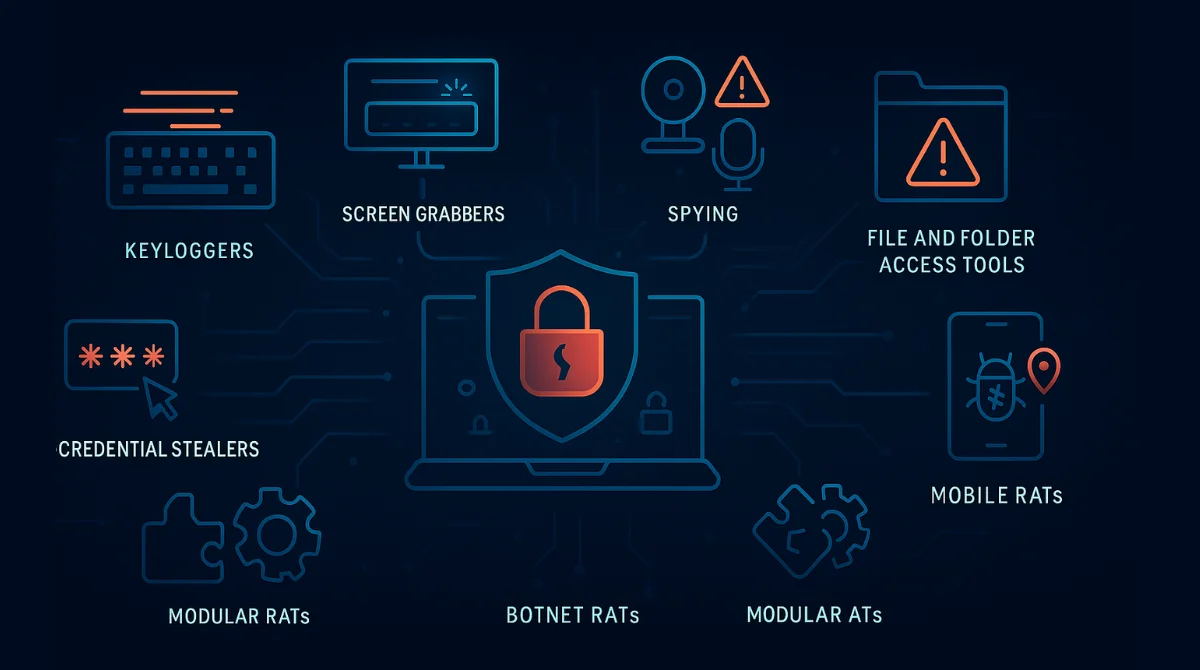
Just like there are different types of apps for different tasks, there are various kinds of Remote Access Trojans, each designed for specific purposes. Some RATs are basic, while others are highly advanced and dangerous. Below are some of the most common types:
1. Keyloggers
These RATs are designed to record every keystroke you make. Hackers use them to steal passwords, credit card numbers, and private messages. It will operate in the background without you ever realizing it.
2. Screen Grabbers
This type takes screenshots of your screen without permission. Hackers use them to see what websites you visit, what you’re working on, and even capture sensitive information like online banking details.
3. Webcam and Microphone Recorders
Some RATs can silently turn on your webcam or microphone to spy on you. They might record videos, take pictures, or listen to your conversations without the camera light turning on.
4. File and Folder Access Tools
These allow attackers to explore your computer’s files and folders. They have the ability to alter, remove, or copy your personal files, including papers and pictures.
5. Credential Stealers
These are designed to look for saved passwords in your browser or apps. Once they collect your login details, hackers can break into your social media, email, bank accounts, and more.
6. Botnet RATs
These connect your device to a larger network of infected machines called a botnet. Hackers use these botnets to send spam, carry out attacks, or spread more malware across the internet.
7. Mobile RATs
Targeting smartphones and tablets, mobile RATs can read your messages, steal contacts, access your camera, and track your location. They’re often hidden inside fake apps or games.
8. Modular RATs
These are advanced RATs that download new tools as needed. They start small and quiet, then expand by adding more spying or damaging features later on, making them harder to detect.
How Do RATs Infiltrate Your System?
RATs can enter your system through various deceptive methods:
- Phishing Emails: You might receive an email that appears to be from a trusted source, prompting you to download an attachment or click on a link. Doing so can install a RAT on your device.
- Malicious Downloads: Downloading software, games, or media from unverified sources can be risky. Some files may contain hidden RATs that activate upon installation.
- Exploiting Vulnerabilities: Outdated software or operating systems can have security gaps. Cybercriminals exploit these weaknesses to install RATs without any user interaction.
- Infected USB Drives: Plugging in an unknown or compromised USB drive can introduce a RAT into your system.
What Can a RAT Do?
Once a RAT is installed, it grants the attacker extensive control over your device. Here’s what they can do:
- Access Personal Files: They can browse, copy, or delete your documents, photos, and other files.
- Monitor Keystrokes: By recording what you type, attackers can capture sensitive information like passwords and credit card numbers.
- Control Hardware: RATs can activate your webcam or microphone, allowing attackers to spy on you.
- Install Additional Malware: They can download and install other malicious programs, compounding the threat.
- Use Your Device for Attacks: Your computer can be used to launch attacks on other systems, spread malware, or participate in coordinated cyberattacks.
Real-World Examples
RATs have been used in various cybercrimes:
- Firebird RAT: An Australian man was charged for developing and selling this RAT, which was embedded in video game modifications to steal data from gamers.
- Warzone RAT: A man in Malta was arrested for selling this RAT and training others in its use, enabling unauthorized access to victims’ computers.
How to Detect a RAT Infection?
Identifying a RAT on your system can be challenging, but certain signs may indicate its presence:
- Unusual System Behavior: Your computer may slow down, crash, or behave erratically.
- Unexpected Network Activity: High data usage or unknown programs accessing the internet could be a red flag.
- Unauthorized Access: Files may be modified or deleted without your input.
- Active Webcam or Microphone: If these devices activate without your consent, it could indicate a RAT is in control.
Protecting Yourself from RATs
Prevention is the best defense against RATs. Here are steps you can take:
- Install Reliable Security Software: Use reputable antivirus and anti-malware programs, and keep them updated.
- Maintain Software Updates: To fix security flaws, upgrade your operating system and apps on a regular basis.
- Be Cautious with Emails and Downloads: Avoid opening attachments or clicking on links from unknown sources.
- Create Strong, One-of-a-Kind Passwords: Create complicated passwords and change them frequently.
- Enable Firewalls: A firewall can block unauthorized access to your system.
- Regular Backups: Back up important data to an external drive or cloud service to prevent data loss.
- Educate Yourself: Keep up with the latest developments in cybersecurity best practices and threats.
What to Do If You’re Infected?
If you suspect your computer has a RAT, don’t panic. Follow these steps:
- Disconnect from the Internet: This stops the hacker from accessing your device.
- Run a Full Antivirus Scan: Let it find and remove the threat.
- Check Installed Programs: Look for anything you didn’t install.
- Change Your Passwords: From a clean device, change all important passwords.
- Reset Your System: If the infection is deep, consider reinstalling Windows or doing a factory reset.
- Contact an Expert: If you’re unsure, a cybersecurity professional can help.
RATs on Mobile Devices
It’s not just computers phones can get RATs too. Android phones are more at risk because you can install apps from outside the Play Store. Mobile RATs can:
- Read your messages
- Record calls
- Access photos
- Track your location
- Listen through the microphone
Always avoid installing apps from unknown sources, and use mobile security apps to stay safe.
Are All RATs Illegal?
Interestingly, not all RATs are created with bad intentions. Some are used for IT support or employee monitoring with permission. But when used without consent, they become illegal and highly dangerous. Selling or using RATs to spy on people can lead to criminal charges.
Conclusion
Remote Access Trojans are a serious threat in the digital world, capable of compromising your privacy and security. By understanding how they operate and taking proactive measures, you can safeguard your devices and personal information against these stealthy intruders.