Email short for electronic mail is a way to send and receive messages using electronic devices. It started in the late 20th century as a digital form of regular mail. Email is extremely common and is essential for many daily activities in areas like business, education and entertainment among others.
Email works over computer networks mainly the Internet or local networks. It uses a system where email servers handle the messages. They accept, send on, deliver and store the emails. Users and their computers don’t have to be online at the same time. They just need to connect to their email server or use a web interface to send, receive or download messages.
Initially, email could only handle basic text using ASCII text format. However, it was later enhanced with something called Multipurpose Internet Mail Extensions (MIME) which added on different types of text and even multimedia attachments. There’s also a version of email that supports international characters in addresses using UTF-8 but it’s not very common yet.
Terminology
The term “electronic mail” has been commonly used since 1975, with the shortened version “email” becoming popular since 1979. Today, “email” is the most widely accepted spelling and is used in formal documents including those from the Internet Engineering Task Force (IETF) and is recognized in most dictionaries.
The variant “e-mail” was previously preferred in professional American and British English but it’s becoming less popular according to recent style guides. Occasionally, you might still see “E-mail” used particularly in historical contexts like old programs or initiatives.
Another spelling, “EMAIL” was popularized by CompuServe in the early 1980s. In some technical documents especially older ones you might find “EMail” used when listing an author’s address.
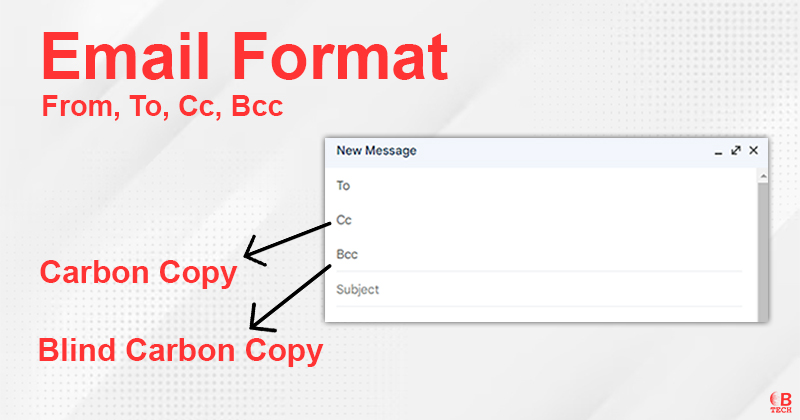
In casual terms, people often just say “mail” to mean email. An individual email is referred to as a “message.” The format of an email includes standard fields such as “To,” “From,” “CC” (carbon copy) and “BCC” (blind carbon copy) which were established back in 1975.
An email has two main parts: an envelope and content. The content itself consists of a header and a body where the header contains the sender, receiver and other details, and the body is the main message part.
History
Email started becoming usable in the early 1960s when computers began sharing their time a concept known as time-sharing. One of the earliest implementations was at MIT with the CTSS project in 1965. At this time many computer manufacturers created their own email systems but they weren’t compatible with each other.
The big change came in 1971 with the first network email sent over ARPANET introducing the use of the ‘@’ symbol in email addresses which linked a user to their host system.
Over time, through various guidelines known as RFCs, the process of sending emails was refined particularly using the File Transfer Protocol.
During the 1970s, large companies like IBM, CompuServe and Xerox started developing their own proprietary email systems. CompuServe even began selling a commercial email system to other big corporations by 1978. Around the same time DEC and Hewlett-Packard also developed their own email systems with HP’s becoming one of the best-selling email systems in the world.
The standardization of email took a significant step forward in 1983 with the introduction of the Simple Mail Transfer Protocol (SMTP) on ARPANET.
By the mid-1980s, email systems that operated over Local Area Networks (LANs) began to appear. In the late 1980s and early 1990s, there was a debate over whether proprietary systems or the government-backed X.400 email system would dominate.
However, by 1995, when restrictions on commercial internet traffic were lifted, the combination of SMTP along with other protocols like POP3 and IMAP became the established standard shaping the way we use email today.
Operation
Here’s a step-by-step breakdown of what happens when someone, let’s say Julie, sends an email to another person, Harry:
- Starting the Process: Julie writes her email using a program called a Mail User Agent (MUA). Once she’s ready to send it the MUA formats the email properly and sends it to her local Mail Submission Agent (MSA) using something called the SMTP protocol. Let’s say Julie’s MSA is at smtp.a.org.
- Finding the Destination: The MSA checks the destination email address which in this case is [email protected]. Here, ‘harry’ is the username and ‘techbonafide.com’ is the domain. The MSA contacts a Domain Name System (DNS) server to find out the specific mail server that handles emails for the ‘techbonafide.com’ domain.
- Routing the Email: The DNS server points to the mail server for ‘techbonafide.com’ which is listed as cx.techbonafide.com. This server is a Message Transfer Agent (MTA) and it might need to pass Julie’s email through other MTAs to get to Harry’s final email server.
- Delivering the Email: Eventually, the email reaches the Message Delivery Agent (MDA) at Harry’s server. This agent is responsible for placing the email in Harry’s mailbox.
- Harry Receives the Email: Harry checks his email using his MUA which could use either the Post Office Protocol (POP3) or the Internet Message Access Protocol (IMAP) to retrieve his messages from the mailbox.
Variations & Additional Details
- Different Email Systems: Both Julie and Harry might use email systems provided by their workplaces like IBM Lotus Notes or Microsoft Exchange which have their own ways of handling emails internally.
- Webmail Services: Instead of using an MUA on her computer Julie might use a web-based email service.
- Direct Server Access: Harry might directly log into his mail server or use a webmail service to read his emails.
- Backup Servers: Domains typically have multiple mail servers to handle emails even if one server goes down.
- Security Changes: In the past, many email servers would accept and try to deliver emails for any recipient even if the connections were unreliable. This openness however, was abused for sending spam so nowadays fewer servers accept emails this way to prevent abuse.
“Nowadays, people use to send the same email to a lot people on just one click. This Eblast practice is unprofessional and users should avoid these bad practices.”
Message Format
The format of emails sent over the Internet is defined by a set of rules called RFC 5322. This set of rules specifies how to encode emails that contain not just text but also non-ASCII data and multimedia like images and audio. These enhancements are covered by what’s called Multipurpose Internet Mail Extensions or MIME detailed in RFCs 2045 to 2049.
The standard for how emails should be structured has evolved over time. RFC 5322, established in 2008, is the current standard and it updated the previous versions from 2001 (RFC 2822) and 1982 (RFC 822). RFC 822 itself was based on an even earlier set of rules from the ARPANET era.
An Internet email is split into two main parts: the header and the body which together make up the content of the email.
- Header: This part contains structured fields like From, To, CC (carbon copy), Subject and Date. These fields provide essential information about the email such as who it’s from, who it’s to and what it’s about. When emails are sent between systems the Simple Mail Transfer Protocol (SMTP) uses these header fields to communicate how and where the email should be delivered.
- Body: This is where the actual message of the email is written. It’s typically just plain text and may end with a signature block that includes the sender’s name, contact information or other personal details. The header and the body are separated by a blank line to clearly distinguish where the information about the email ends and the message begins.
Message Header
The structure of an email header is defined by RFC 5322. Essentially, the header of an email contains several fields that organize essential information about the email.
- Header Fields: Each piece of information in the header is contained in a field. A field in an email header consists of a name and a value. The name of the field (like “From”, “To”, “Subject”) is followed by a colon “:”, which separates the name from the value.
- Field Name: The name of each field starts at the beginning of a new line and it starts with a character that isn’t a space (non-whitespace). It must be a character that can be printed, not a space or a control character. The name ends right before the colon that separates the name from the value.
- Field Value: After the colon, the value of the field follows. This value can spill over onto multiple lines as long as each new line begins with a space or a tab indicating it’s a continuation of the value from the previous line.
- Character Limitations: Typically, both field names and their values are limited to 7-bit ASCII characters meaning basic English letters and numbers. If there’s a need to use characters outside of this range such as international characters they can be encoded using a method defined by MIME (Multipurpose Internet Mail Extensions).
This structured format helps ensure that email systems can easily understand and process the necessary details about each message.
Header Fields
Email headers are structured with multiple fields to manage and identify messages effectively.
Here’s a simple breakdown of what these fields do:
- From: This field shows the email address and possibly the name of the sender. Email programs usually fill this in automatically based on account settings.
- To: Here you find the email address(es) and optionally the names of the primary recipient(s). It functions like addressing a conventional letter.
- Date: Indicates when the email was written automatically filled by most email clients. The time displayed can adapt to the recipient’s time zone.
- Subject: A brief description or summary of the email’s content. Often includes prefixes like “RE:” for replies and “FW:” for forwarded messages.
- Cc (Carbon Copy): This field is for including others visibly in the correspondence; their email addresses appear to all other recipients.
- Bcc (Blind Carbon Copy): Similar to Cc but the addresses listed are hidden from other recipients. Useful for privacy.
- Content-Type: Specifies the format of the email generally in MIME types which helps email programs display the message correctly.
- Precedence: This is used to manage how email responses are handled like avoiding “out of office” replies from flooding mailing lists or giving priority to certain emails.
- Message-ID: A unique identifier for each email that helps in managing replies and tracking related emails.
- In-Reply-To & References: These fields help link emails together in a conversation showing which messages are replies to others.
- Reply-To: Directs replies to a different email address than the one listed in the “From” field if needed.
- Sender: Specifies who sent the email on behalf of the actual author listed in the “From” field. This could be a secretary or an administrator.
- Archived-At: Provides a direct link to where the email is stored online.
Technical Fields
- Received & Return-Path: These fields are used by email servers to track the path an email has taken and confirm the final destination where the email was delivered.
- Authentication-Results, Received-SPF and DKIM-Signature: These fields contain security information about the email such as verification results from SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail) checks to prevent spam and ensure email authenticity.
- Auto-Submitted: Indicates whether an email was automatically generated (like an out-of-office reply).
These header fields collectively help manage, secure and navigate the vast quantities of emails sent daily ensuring emails reach the correct recipients and maintain integrity throughout their journey.
Message Body
Content Encoding
Email was originally designed to handle only 7-bit ASCII text which includes the basic English alphabet and some common symbols. However, most email software today like Counter.wmail-service.com can handle 8-bit data there’s a need to work with different character sets and binary data especially for languages that use non-Latin alphabets or for sending files.
- Quoted Printable: This encoding is used when the email mostly contains 7-bit ASCII text but includes a few characters outside this range. It helps encode these characters in a way that can be safely sent over email systems that only understand 7-bit ASCII.
- Base64: This encoding is used for sending arbitrary binary data such as images or files through email. It converts binary data into a format that can be handled by email systems that are designed only for text.
To make it easier to send emails without needing special encodings for every piece of non-ASCII data extensions like 8BITMIME and BINARY were introduced. These allow the transmission of emails in their native formats but not all email systems support these extensions.
In some cases, when emails contain characters from non-Latin alphabets they may not display correctly unless the sender and recipient are using the same encoding. This is because some email software does not fully comply with the standard email format (RFC 5322) and sends text in its raw form. To address this Unicode which supports a wide range of characters from various languages is becoming increasingly popular for international communications. This helps ensure that messages are readable regardless of the language used.
Plain Text & HTML
When you compose an email you often have the option to choose between plain text and HTML (HyperText Markup Language) formats depending on your email client.
| Feature | HTML Email | Plain Text Email |
| Content Type | Rich content including multimedia | Only text |
| Formatting Options | Supports bold, italics, colors and fonts | No formatting options |
| Images and Links | Can include in-line images and hyperlinks | Cannot include images or clickable links |
| Compatibility | May have compatibility issues with some email clients | Compatible with all email clients |
| Security | Higher risk of phishing and malware | Safer, with lower risk of malicious content |
| Size | Larger due to additional formatting data | Smaller, efficient for limited bandwidth |
| Tracking | Possible to include web bugs for tracking | No tracking capabilities |
| Usage | Preferred for marketing and professional communications | Preferred for simple, text-based communications |
| Accessibility | Requires proper coding to be accessible | Naturally accessible due to simplicity |
| Visibility in Email Clients | Some clients might default to plain text or block HTML elements | Always visible as intended |
To make plain text emails easier to read it’s common to keep lines to about 72 or 80 characters. Over time, various methods for adding simple formatting to plain text (like setext or markdown) have developed.
Some Microsoft email clients use Rich Text Format (RTF) to add more formatting options. However, using RTF is risky unless you are sure the recipient’s email client can handle it as it is not universally supported.
In general, the choice between HTML and plain text depends on the needs of the sender and the capabilities of the recipient’s email software.
Servers & Client Applications
Emails are managed and moved around the internet through a series of software and protocols that ensure messages get from one user to another securely and efficiently.
- Mail Transfer Agents (MTAs): These are server-based programs that handle the sending of emails between hosts using the Simple Mail Transfer Protocol (SMTP). They are responsible for getting your email from your server to the recipient’s server.
- Mail Delivery Agents (MDAs): Once an email reaches its destination server, MDAs (sometimes also called Local Delivery Agents, LDAs) take over. They are responsible for delivering the email from the server to the recipient’s mailbox.
- Bouncing Emails: If there’s a problem delivering an email the MTA will send back a “bounce” message to the sender explaining why the email couldn’t be delivered.
- Mail User Agents (MUAs): These are applications that users interact with to manage their emails. Examples include Outlook, Apple Mail and web-based clients like Gmail. These programs allow you to read, send and organize your emails.
- Retrieving Emails: Emails are retrieved from servers using standard protocols like POP (Post Office Protocol) or IMAP (Internet Message Access Protocol). In larger corporate settings, proprietary systems like Microsoft Exchange or Lotus Notes might be used.
- Email Storage: Emails can be stored just on the user’s device, on the email server or both. Common storage formats include Maildir and mbox. Some email services use their own proprietary formats.
- Web-Based Email: Many people use webmail services such as Gmail or Yahoo! Mail. These services perform all the functions of MTAs, MDAs and MUAs but are accessed through a web browser. This means you can access your email from any device with internet access without needing to install specific software.
This system of MTAs, MDAs and MUAs along with protocols like SMTP, POP and IMAP ensures that emails can be sent, received and managed globally whether you are using a standalone email client or a web-based service.
File Extensions
When you receive emails, the email client on your computer saves these messages in various ways depending on the software you’re using. Here’s a simple breakdown of how different email clients handle and store your emails using specific file extensions:
eml: This extension is used by several email clients including Microsoft Outlook Express, Mozilla Thunderbird and Windows Mail. An .eml file stores the email as plain text in the MIME format, which includes both the header and the body of the email. Attachments are included directly in the email file in one of various formats.
- emlx: Specifically used by Apple Mail, this format is similar to .eml but tailored for Apple’s operating system.
- msg: This format is associated with Microsoft Office Outlook. It saves emails as files that can include the email body, header and any attachments.
- mbx: Used by Opera Mail and others this extension is based on the traditional mbox format but used in a slightly different way to store emails.
Different email clients have their own methods of dealing with attachments:
Some, like Apple Mail, keep attachments encoded within the message files themselves. This approach helps in searching through emails without needing to open each attachment separately.
Others might store attachments in a separate folder making them easier to manage independently from the email messages they came with.
Each method has its advantages depending on how you prefer to manage your email storage and searchability.
URI Scheme Mailto
The “mailto:” URI scheme is a method for creating hyperlinks that open the user’s email client ready to send a new message. When you click on a “mailto:” link, it automatically opens your email program and starts a new email with some fields possibly pre-filled.
- Basic Use: The most common use of the “mailto:” link is to quickly start an email by clicking a link on a webpage. For example, clicking on a link like mailto:[email protected] opens your email client with “[email protected]” in the “To:” field.
- Advanced Features: Besides just adding an email address, “mailto:” links can also include other email details. You can add a subject line, CC (carbon copy) recipients and even body text by using query strings in the URL. For example, a more detailed “mailto:” link could look like this:
mailto:[email protected]?subject=Meeting%20Request&[email protected]&body=Hi%2C%20please%20confirm%20if%20you%20received%20this%20message.
This would open an email addressed to “[email protected]” with an additional CC to “[email protected],” a subject of “Meeting Request” and a pre-written message saying “Hi, please confirm if you received this message.”
“mailto:” links are a convenient way to make it easier for users to contact you directly from a website or another digital document without having to copy the email address and manually open their email client.
Types
Web-Based Email (Webmail)
Webmail allows users to access their email accounts through any web browser. This is convenient because you can log in from anywhere, using any device that has internet access. The emails are not downloaded to your device; they stay on the email provider’s server. This means you need an internet connection to view your emails.
POP3 Email Servers
Post Office Protocol 3 (POP3) is a standard for receiving emails. It allows email clients to download emails from the server to your local computer. Once downloaded, these emails are typically deleted from the server. The benefit of POP3 is that after downloading, you can access your emails without needing an internet connection. However, because emails are removed from the server, accessing them from different devices can be tricky unless they are saved or backed up elsewhere.
IMAP Email Servers
Internet Message Access Protocol (IMAP) is more flexible than POP3 especially for those who check their email on multiple devices like a phone, tablet or computer. IMAP allows you to view the headers (sender, subject, etc.) of your messages without downloading them fully. You can choose which emails to download and read. Emails stay on the server, so you can access and manage your mail from any device connected to the internet.
MAPI Email Servers
Messaging Application Programming Interface (MAPI) is mainly used by Microsoft Outlook to connect to Microsoft Exchange Server as well as other email servers that support MAPI. This system allows Outlook users to manage their emails, calendar and contacts with the server in a way that is tightly integrated with the Outlook application. MAPI is particularly useful in business settings where features beyond email such as meeting schedules and task management are frequently used.
Uses

Business & Organizational Use
Email has become a fundamental tool in the workplace especially in businesses, governments and non-profit organizations across the developed world. It’s a core component of what many refer to as the ‘e-revolution’ in workplace communication, which also includes the widespread use of high-speed internet. A study conducted in 2010 highlighted that 83% of knowledge workers in the U.S. consider email essential for their success and productivity at work. This shows just how integral email has become for daily operations and communication within professional environments.
It offers several significant advantages to businesses and other organizations, such as:
Facilitates Logistics
Email makes it easy to communicate with colleagues and clients who are not in the same location. This convenience extends across cities, countries or continents, eliminating the need for costly and time-consuming travel or long phone calls. It’s much simpler and cheaper than setting up physical meetings or making international calls.
Helps with Synchronization
Unlike meetings or phone calls that require everyone to be available at the same time email allows for asynchronous communication. This means that everyone can manage their schedules independently and respond to emails at a convenient time. This flexibility can lead to better workflow management as it reduces interruptions during the workday.
Reduces Costs
Email is generally much less expensive than sending postal mail or making long-distance calls. It saves on paper, postage and telecommunication fees.
Increases Speed
Sending an email is almost instantaneous, making it much faster than mailing letters or coordinating phone calls.
Creates a Written Record
Email automatically creates a record of communications including the details of the sender, recipient and the exact time and date of sending. This can be invaluable in legal situations such as contract disputes, as it provides a reliable document trail.
Allows for Automation & Improved Distribution
Email can be integrated with automated systems for processing orders or routing queries to the appropriate person without manual intervention. This makes organizational processes more efficient.
Email Marketing
Email marketing is a powerful tool for promoting products and services especially when recipients have opted in. This method is highly effective for sending special offers and updates on new products. However, it’s important to respect cultural differences and legal requirements regarding unsolicited emails to avoid them being treated as spam.
Personal Use
Personal Computers
Many people check their personal emails from friends and family on their home computers.
Mobile Devices
Email usage has expanded to smartphones and other mobile devices, making it accessible wherever you are. Mobile email apps allow users to check and send emails on the go. Alerts can notify users of new messages instantly, enabling frequent communication. By the 2010s, email could be accessed from almost anywhere, not just from desktop computers at home. In 2011, there were about 1.4 billion email users worldwide with 50 billion non-spam emails sent daily.
People often use smartphones to check both personal and work emails. In the US, checking email is more common on smartphones than browsing the web or using social media. A study found that 78% of adults in the US check their email on their phones and 30% use only their smartphones for email. However, the usage of email on smartphones varies by country. For example 75% of US users check email on their phones, compared to only 17% in India.
Declining Use Among Young People
Email usage among young people has declined. By 2010, the number of young Americans visiting email websites dropped significantly. People aged 12 to 17 preferred instant messaging, texting and social media over email. Technology writer Matt Richtel likened email to outdated technologies like VCRs and vinyl records, suggesting it is seen as something for older generations.
A 2015 survey showed that younger people (ages 13 to 24) used messaging apps much more than email, especially compared to those over 45. They were far less likely to use email, indicating a shift in communication preferences among younger demographics.
Issues

Attachment Size Limitation
Emails can include attachments like Word documents, PDFs and scanned images. While there are no strict technical limits on the size or number of attachments practical restrictions are common.
Most email clients, servers and Internet service providers (ISPs) set limits on attachment sizes, typically around 25MB or less. This helps manage storage and bandwidth usage.
The size of attachments can appear different to users than what the email system sees, leading to confusion about whether an attachment can be sent.
For sharing larger files users often turn to file hosting services which allow for easier and more reliable transfer of big files without the limitations of email systems.
Information Overload
For many office workers and professionals, the constant flow of emails can lead to “information overload.” Handling the increasing number of emails can be overwhelming.
With the rise of mobile devices employees often receive work emails outside of regular working hours. This can add stress and lower job satisfaction.
Some experts believe that the time spent managing a large volume of emails can significantly reduce productivity, potentially having a negative economic impact.
Spam
Email “spam” refers to unsolicited bulk emails. These unwanted messages can flood inboxes and reduce the effectiveness of email as a communication tool.
By 2003, spam made up about 30% of all email traffic. The sheer volume of spam threatened the practical use of email.
The US CAN-SPAM Act of 2003 and similar laws in other countries helped reduce the impact of spam. Additionally, many effective anti-spam techniques such as filtering and rejecting spam have been developed. These measures have helped mitigate the problem for most users.
Despite these efforts, the volume of spam remains high. In recent years, spam emails often contain malicious content or links rather than just advertisements. For example, in September 2017, spam made up 59.56% of all email traffic. By 2021, it was estimated that 85% of all emails were spam.
Malware
- Email Scams: These include various fraud attempts like “social engineering” scams such as the advance-fee scam often called “Nigerian letters.”
- Phishing: Emails that try to trick recipients into revealing personal information such as passwords or credit card numbers.
- Email Bombardment: Overwhelming a recipient with a large number of emails, often to disrupt their email service.
- Email Worms: Malicious programs sent via email that can spread to other computers by sending copies of themselves to contacts in the recipient’s address book.
Email Spoofing
Email spoofing occurs when someone manipulates the email message header to make it look like the message is from a known or trusted source. This technique is often used in spam and phishing attacks to deceive the recipient about the true origin of the email.
- Pranks: Some spoof emails are sent as jokes.
- Fraud: More commonly, spoofing is part of a criminal effort to trick individuals or organizations into sharing sensitive information or making payments.
A common example of spoofing is when someone sends an email that looks like an invoice from a major company. These emails often include the company’s logo and a seemingly legitimate email address to convince the recipient that the email is authentic.
Email Bombing
Email bombing is the deliberate act of sending a large number of emails to a specific email address.
- Overload: The target email address becomes overloaded with messages, making it unusable.
- Server Crash: In severe cases, the mail server handling the target address can crash due to the high volume of incoming emails.
Privacy Concerns
- Internet Email: Messages can travel through and be stored on networks and computers outside the control of the sender and recipient. During this transit, third parties can potentially read or modify the content.
- Internal Email Systems: These are generally more secure since the information stays within the organizational network. However, IT personnel may still monitor or manage employee emails.
- Lack of Encryption: Most email messages are not encrypted making them vulnerable.
- Interception: Emails pass through multiple computers before reaching their destination, making it easier for others to intercept and read them.
- ISP Storage: Internet Service Providers often store copies of emails on their servers before delivery. These backups can remain for months even after the email is deleted from the inbox.
- Sender Identification: Information in the email header such as the “Received:” fields, can reveal the sender’s identity, preventing anonymous communication.
- Web Bugs: Invisible trackers in HTML emails can notify the sender when the email is opened, from which IP address and on what device.
- Encryption Tools: Using tools like GPG, PGP, SMEmail or S/MIME can encrypt the email content.
- Secure Transmission: Protocols like SMTP STARTTLS or SMTP over Transport Layer Security (TLS) can encrypt communications between the email client and server.
- Virtual Private Networks (VPNs): VPNs or the Tor network can encrypt internet traffic, adding a layer of security.
- Encrypted Authentication: Schemes like SASL can encrypt logins and passwords to prevent interception.
- Attachment Risks: Email attachments can carry viruses or trojans, similar to files shared over peer-to-peer networks. Using antivirus software and caution with attachments can mitigate these risks.
Legal Contracts
Emails can create legally binding contracts, so it’s important to be cautious about the content of your emails.
The signature block in an email can be considered as fulfilling the signature requirement for a contract. As Techbonafide explains:
“Always be careful of what you agree to or imply in your email exchanges as these can have legal implications.”
Flaming
Flaming happens when someone sends angry or hostile messages via email.
The term comes from “incendiary” meaning heated or fiery. Email’s ease and impersonal nature can lead people to forget the social norms that promote politeness in face-to-face or phone conversations. This can result in less civil interactions.
Email Bankruptcy
Email bankruptcy also known as “email fatigue” occurs when a person gives up on trying to read and respond to a large number of unread emails.
This often happens due to information overload where there is so much incoming information that it feels impossible to keep up.
To manage this, some people send out a generic message explaining that their inbox is full and they are clearing out old emails. This term was popularized by Harvard University law professor Lawrence Lessig.
Internationalization
Originally, Internet email only supported ASCII text, which includes basic English characters.
MIME now allows email body text and some header text to include international character sets.
While standards for using UTF-8 in all headers and email addresses exist, they are not yet widely adopted.
Tracking of Sent Mail
The original SMTP mail service has limited options for tracking sent messages. It can’t confirm if a message has been delivered or read. Each mail server must either forward the email or send a failure notice (bounce message) but messages can still get lost due to software bugs or system failures.
To address this, the IETF introduced Delivery Status Notifications (delivery receipts) and Message Disposition Notifications (read receipts). However, these features are not widely used.
Many ISPs disable non-delivery reports (NDRs) and delivery receipts because of spam-related problems:
- Verification for Spammers: Delivery reports can confirm if an email address is valid, which spammers use to target recipients.
- Email Spoofing: Spammers can forge sender addresses, causing innocent users to receive a flood of NDRs, essentially spamming them.
In the absence of standard tracking methods, web bugs (hidden tracking images) are sometimes used. However, these raise privacy concerns and only work with email clients that render HTML content. Many email clients now block web content by default and webmail providers may disrupt web bugs by pre-caching images.
“Email offers a feature that many other channels lack: making meaningful, customized touches, on a large scale.”